All of us have experienced spam. Spam is unsolicited and unwanted email that arrives in our inboxes. It can range from a minor annoyance to complete disruption of email accounts, or worse yet, can harbor malware, trojans, and viruses.
Some of us go through a period of time where we do not get spam in our inbox, then are suddenly bombarded with it. Some of us even incorporate spam/content filters, often decreasing unwanted and unsolicited email, only to have a renewed surge of spam activity within a year or so.
While our first instinct may be to contact our email administrators to inform them of increased activity and find out if any email server settings have been modified, let’s not forget our own responsibilities to help prevent, diminish, and combat spam from infiltrating our email accounts.
I want to bring up four points that we all need to think about when we want to protect ourselves from these disruptive and intrusive emails.
First, whenever possible, try to avoid using your primary email address when filling out forms. We see it all the time, at the mall or shopping center a booth is offering a free entry to win a prize. We eagerly fill out all the information to win that car or vacation to the Bahamas, and one of the pieces of information they ask for is our email address.
For things like these, try to use an email address that is not your primary email address. Set up a Yahoo or Gmail account that is used solely for these events, and it will help to greatly reduce the amount of spam that arrives in your inbox.
You might think that creating an alternative email address on your primary email domain will solve the problem. For example, your primary email account is [email protected], and you create [email protected]. The problem with this method is that you are disclosing your email domain, and spammers can now bombard @domain.com with “guessed” addresses (such as info@, webmaster@, or even entire dictionaries of usernames) which can eventually spill over to your primary email address.
Second, look at this one as a duty or responsibility: never respond to spam! Delete it, and whenever possible, mark it as spam in your email system so that you build a reputation for what is and isn’t spam. The next time you get a similar spam message it will automatically drop it in your “Trash” or “Junk” folder.
In SmarterMail, if you see an email in your inbox that is spam you can go to Actions/Mark/spam. The more you use this, the more you build up your definition of potential spam.
The third good practice is setting up account level spam and content filtering rules. Many email systems have this feature. In SmarterMail you can go to Settings/Filtering. There you can define your own content filtering and spam filtering rules.
Don’t forget Greylisting! When an email network “greylists” messages, they do not accept the initial incoming message, but rather instruct the sending mail server to try to delivery again later (which most servers will do every few minutes). The assumption being that spam servers will not attempt to send the message again, but legitimate servers will. Greylisting will delay legitimate emails though, so it’s up to you to decide to enable or disable this feature. For the most part, Greylisting is a valuable tool in helping keep your email account clean of unsolicited emails.
Finally, if at all possible, try to avoid “catch-all” email accounts. Catch-all accounts will allow any email address to come through. For example, if you have Catch-all enabled, email addresses that do not exist ([email protected], [email protected]) will make it into your inbox. There may be a business need to have this activated, but this will greatly increase the likelihood of receiving spam, even with a strong spam filtering system.
The last thing that I would like to mention is the necessity of remaining diligent.
Many of us successfully implement the above practices, reducing or even eliminating spam from getting into our inboxes, only to relax our guard, even temporarily, exposing us to a new series of attacks on our email.
Keep in mind that spam is an ongoing threat, and that spam is adaptive and always evolving. Spammers know that they have to constantly update their procedures and techniques to get through to the greatest number of people.
One of the biggest mistakes that we can make is believing that once we have effective anti-spam measures in place, that we do not have to revisit and update those measures. If that were true, spam would have been eliminated a long time ago.
As spammers find new and more sophisticated ways to infiltrate your inbox, you have to remain vigilant and active in combating spam.
I know you absolutely love the SmarterMail webmail that we provide with your account. What’s not to love? It’s old fashioned, clunky, confusing – perfect!
But you don’t have to be stuck with it. You can “pop” your email boxes using Gmail. “Pop” is just nerd slang for “check.” What we’re talking about here is reading and replying to mail that comes in to the addresses that you’ve set up on your domain name, but doing it all through the Gmail interface, and that’s pretty cool.
This is not a tutorial for using Google Apps mail with your domain. We already have one of those in our forum. This tutorial will show you how to keep your mail service here at Winhost, but use Gmail as your email program.
You have a Gmail account, right? If not, go set one up, then we can get started.
Log in to Gmail and click the Settings gear and select Settings.
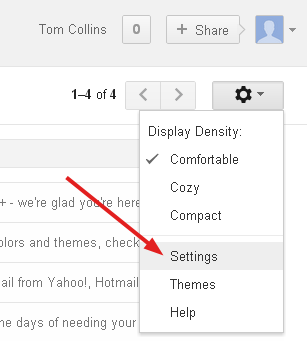
Click Accounts and Import.
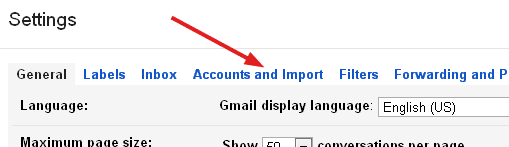
Click Add a POP3 mail account you own. In the lovely orange popup window that opens, enter the email address that you want to check using Gmail. Click Next Step.
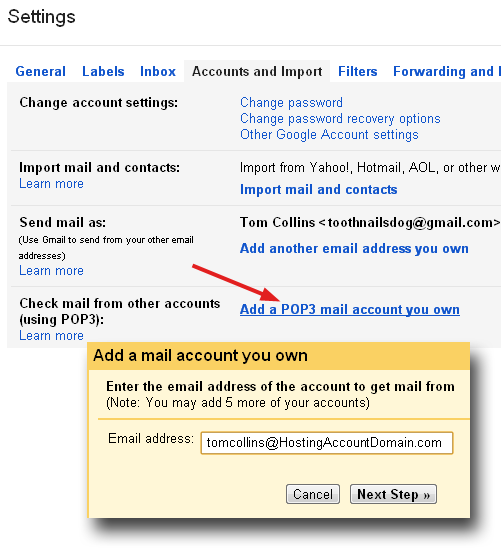
Next you’ll be on the mail settings page of the popup window. There are a lot of variables here (it’s Google, after all), but we’ll concentrate on the simplest, quickest setup.
Username is your complete email address, not just the part before @.
Password is the POP account password that you entered into Control Panel when you set up the email address.
POP Server should be pre-populated with mail.yourhosteddomainname.com.
Everything else can be left in its default state. If you do not intend to use Gmail exclusively, check the box for “Leave a copy of retrieved message on the server,” that will allow you to pull your mail down from another source in addition to Gmail.
But beware, if you use that option and your Winhost email boxes get full, your mail will bounce. To prevent that ever happening, do not check “Leave a copy of retrieved message on the server.”
Click Add Account.
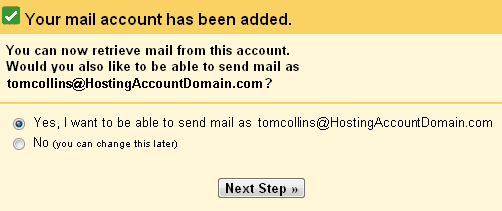
The next window will verify that your account has been added.
It will also ask if you want to be able to send mail “as” the new address. If you intend to use Gmail as your only email client, or if you ever want to respond to the incoming mail for your newly set up account, select Yes, I want to be able to send mail as…
Click Next Step.
If you selected “No” in the previous window, you’re finished.
The end.
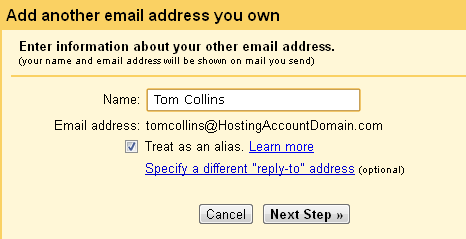
But you didn’t select “No,” did you? Good! You’re going to want to be able to send mail from Gmail “as” yourself.
So in the next window simply enter your name. This is the name you want to appear as the sender. Leave Treat as an alias checked.
Click Next Step.
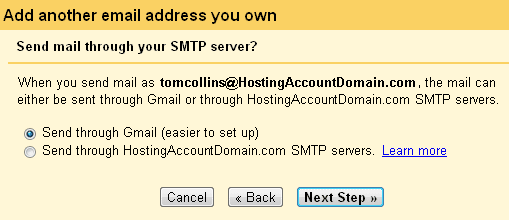
Next the cheerful Google robots are going to ask if you want to send mail through their SMTP server or if you want to send through your domain. It’s much easier to leave the default Send through Gmail checked. And since this is the easy setup guide, that’s just what we’ll do.
Click Next Step.
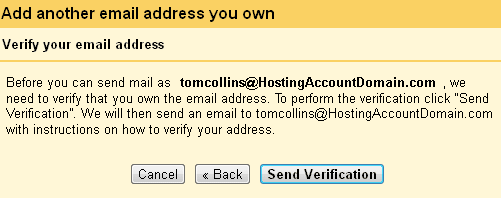
Before Gmail will let you send mail as yourself they want to make sure that you are who you say you are. Otherwise you could send mail as me — or someone important like Scott Guthrie or Larry the Cable Guy. To get the verification ball rolling, just click Send Verification.
Now you could log in to your POP account with your desktop email client, or use SmarterMail webmail to pick up the Google verification email. But since you’re already checking mail for your address using Gmail, you should be able to click Inbox on the upper left side of the Gmail window and – through the miracle of modern technology – pick up the verification email right there.
Try it. I’ll wait here.
Once you’ve copied the verification code from the email, just enter it into the box in the popup window and click Verify.
The popup window will disappear and nothing else will happen.
Which is good, because nothing else needs to happen. You’re all set!
Speaking of Google, why not join our circles on Google+? We’re waiting for you.
Our team has discovered that since the launch of Windows 2012 and IIS 8 there have been some issues with installing and running some of the more popular Content Management Systems such as DotNetNuke and Orchard.
The problem can be resolved by setting the Trust Level to Full in the web.config file. To do this:
If you find that you’re having difficulties with other Content Management Systems, you might want to try setting the Trust Level to Full as well to see if that will correct the problem.
Sitting here this morning, as I run through my daily routines of reviewing sales emails, marketing proposals, SEO reports, and general news, I ran across something that made me stop and pause for a good minute. It was a talk by Steve Jobs from 1983.
This was pre-Macintosh Steve Jobs. This was still the bright eyed Steve Jobs that had yet to be “removed from his managerial duties” by the board of his own company only to come back as it’s long lost savior almost a decade later. A Steve Jobs that had yet to earn the labels of “Futurist” or “Visionary.” This was just Steve Job, a 28 year old kid talking to design conference… yes a design conference.
See, even back in 1983 Jobs saw that design was something that needed to be given equal attention when working with technology. It seems something obvious now, but if you think about technology in 1983, design was the last thing on anyone’s mind. PC computers were large briefcase size things that were gray or tan in color.
Even in his talk Steve Jobs says “If you’ve looked at computers, they look like garbage. All the great product designers are off designing automobiles or they’re off designing buildings. But, hardly any of them are off designing computers.” Even in 1983 Steve was looking to change that.
After giving this a listen, I started thinking about 1983. I was 7 years old and already playing with my Dad’s new Commodore 64 typing out BASIC commands to play a game. And after some digging back, I noticed that 1983 was a big year for technology and the internet:
So, an argument can be made that 1983 was a hallmark year for technology and the internet as we know it today. But yet, with personal computing and the internet still in their infancies, Jobs could see what was about to come and where these things could lead.
Listening to the full talk, plus Q&A after, you can hear Jobs talk about ideas and concepts that can be traced forward 25 years later into truths about how we use technology today and every day products like tablet computers. At the end of the Q&A, Jobs even addresses language and voice recognition, which has only now been adopted by the general public with Siri.
So as I’m typing this we have reached the 1 year anniversary, if you will, of Steve Jobs’ passing. For all his flaws (and there were many) it is hard to deny his ability to see past technical limitations and look forward to what he knew was possible.
I was never an “Apple Fan Boy” growing up. In fact I hated Macintosh computers with a passion all through High School and College only using them when all other options had failed. But I did respect how Jobs saw the world in his eyes and was able to rally people around that vision. Listening to this talk only adds to that respect.