![]()
We interrupt this blog to bring you an announcement regarding a few layout changes in Control Panel.
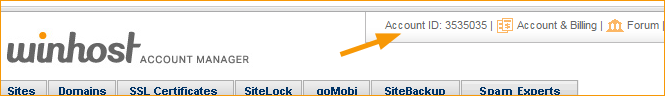
1. The Account ID moved to the very uppermost navigation – next to Account & Billing:
2. The Related KB links on the right side column moved to the bottom – right above the footer:
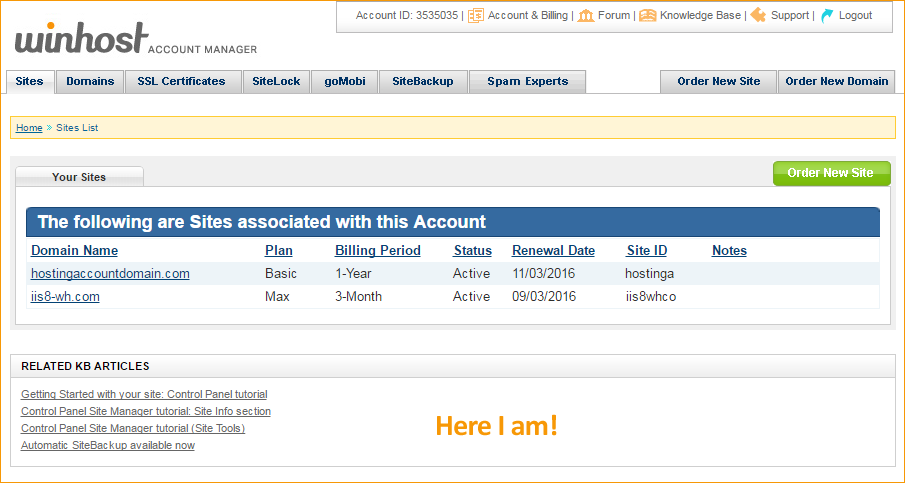
3. For most of the control panel sections, we expanded the main section to span the entire control panel width.
That is all.
Please proceed to have a great weekend.
![]()
When you order an SSL certificate from us, your primary domain name will be secured for free. So, if you order an SSL certificate for www.HostingAccountDomain.com, then HostingAccountDomain.com.com will be added as a Subject Alternative Name automatically.
So you can secure both www.HostingAccountDomain.com and HostingAccountDomain.com with just one certificate.
This works for any subdomain, not just for the www. prefix. You can order a certificate for login.HostingAccountDomain.com and HostingAccountDomain.com will be added to the certificate.
Here’s a sample certificate where you see both the subdomain and the primary domain secured:
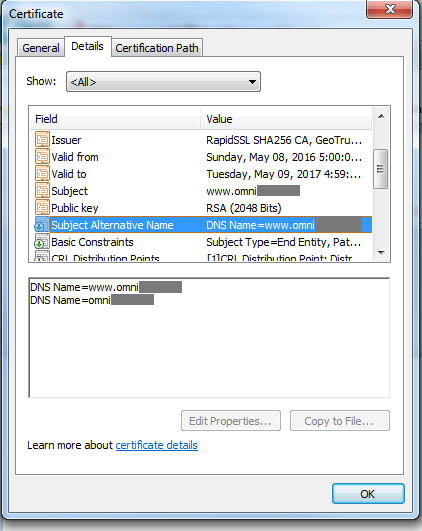
Note that this is only applicable to single-level domains. For example, www.test.HostingAccountDomain.com will not secure test.HostingAccountDomain.com.
This works for all of the certificates available through Winhost!
![]()
Today we’re announcing the availability of SQL 2016. It’s available now in the MS SQL Manager of Control Panel.
The new stretch database feature is enabled and you can learn more here. Some other new features include Query Store, Temporal Tables, and JSON Support.
And of course, there are no extra fees for SQL 2016 hosting.

![]() Today we are introducing 5 new domain extensions into the mix: .cloud, .club, .pro, .store, and .xyz. You can check out our website for domain pricing, or go to Control Panel right now to order a new domain name.
Today we are introducing 5 new domain extensions into the mix: .cloud, .club, .pro, .store, and .xyz. You can check out our website for domain pricing, or go to Control Panel right now to order a new domain name.
We plan to introduce more domain extensions, so if you have any suggestions, please let us know.
![]() We have updated our Windows 2012 servers to support ASP.NET Core 1.0. This is the latest rewrite of ASP.NET from Microsoft (which they had previously called .NET 5). Learn more about .NET Core here.
We have updated our Windows 2012 servers to support ASP.NET Core 1.0. This is the latest rewrite of ASP.NET from Microsoft (which they had previously called .NET 5). Learn more about .NET Core here.
If you want to use .NET Core 1.0 but your site is not on a Windows 2012 server, we can migrate you to a newer server. Just log in to the support portal and open up a ticket. We’ll take it from there. You can see the web server your site is running on in the Site Info section of Control Panel, under “Web Server.”
![]() It’s important to keep your web applications up-to-date. This prevents known vulnerabilities from being exploited and wreaking havoc on your site. That goes for any third-party software you might use on your site, but today we’re going to talk about updating DotNetNuke.
It’s important to keep your web applications up-to-date. This prevents known vulnerabilities from being exploited and wreaking havoc on your site. That goes for any third-party software you might use on your site, but today we’re going to talk about updating DotNetNuke.
The most important thing before upgrading is to back up your current DotNetNuke site. Also, if you are using any third-party themes or modules, please contact the author(s) before upgrading to make sure they are still supported in the latest version of DNN.
Backing up the MS SQL database
This will place the backup of your MS SQL database within the App_Data directory with the file extension “.bak.”
Backing up your web site files via FTP
Downloading the upgrade files and Extracting
Important: you must know your SuperUser account login in order to upgrade.
You can download the Upgrade files through DNN’s download page.
Uploading the updated files
Upgrading
![]()
The latest versions of the following applications are now available through our App Installer tool:
Do you know what ransomware is? It’s a computer compromise, typically spread via a macro in a Microsoft Word file. Those spam “invoices” you get, with a .doc attachment? They’re almost always ransomware. If the macro is run, most of the document and image files on your computer are encrypted, and the hacker then extorts money out of you to get the key. The longer you wait, the higher the price.
Right about now you’re probably thinking, “Not a problem for me, I have backups for all my important files!” Which is good. You can reformat your computer, restore your backups and be done with it. Lesson learned. If you’re not backing up your computer files, now’s the time to start, right? Right? Get started. Seriously.
If that wasn’t bad enough, the people who write ransomware have now figured out how to encrypt your website files and hold them for ransom, and compromises are spreading rapidly across the web. The compromise is done through vulnerabilities in third party applications or your own scripting (out-of-date WordPress sites are a common target – update your WordPress site, plugins and themes!).
At the time we’re writing this, that ransom starts at around $175, and goes up from there the longer you wait. The best way to guard against that is the same way you’ve guarded against site compromise forever: keep your third party application updated, and examine your own code for vulnerabilities.
But if the bad guys do get in and your site files are encrypted and held for ransom, what can you do?
Well, we make site and database backups every day, so we may be able to help you restore the unencrypted version of your files. But our backups are meant for disaster recovery, so there’s often a fee involved with pulling and restoring a copy, and it will take a little time. In addition to that, we only keep a few days of backups. If you don’t notice a ransomware compromise for four or five days, all of our backups will probably be copies of the compromised files, and therefore not useful in restoring the site.
The best answer is maintaining a tight ship, as far as your site is concerned. But a really good standby strategy is our SiteBackup service. It allows you not only to back up website and database files, but to keep multiple versions of those backups for long periods of time. That increases the likelihood that you will have a “clean” backup to restore to defeat the ransomware goons. The best part is you control the backups, they’re available to you immediately any time you need them.
Another cool thing that SiteBackup can do is alert you if Google flags your site as compromised, and automatically disable any further backups. That means you can rest easy that you’ll always have a clean backup for restoration.
Any way you slice it, it’s better to be safe than sorry, so we really recommend checking out SiteBackup. It’s inexpensive (starting at $2.95 a month for 10GB of backup space!), extremely easy to use, and – we think – some of the best peace of mind money can buy.
Activate SiteBackup in Control Panel now.
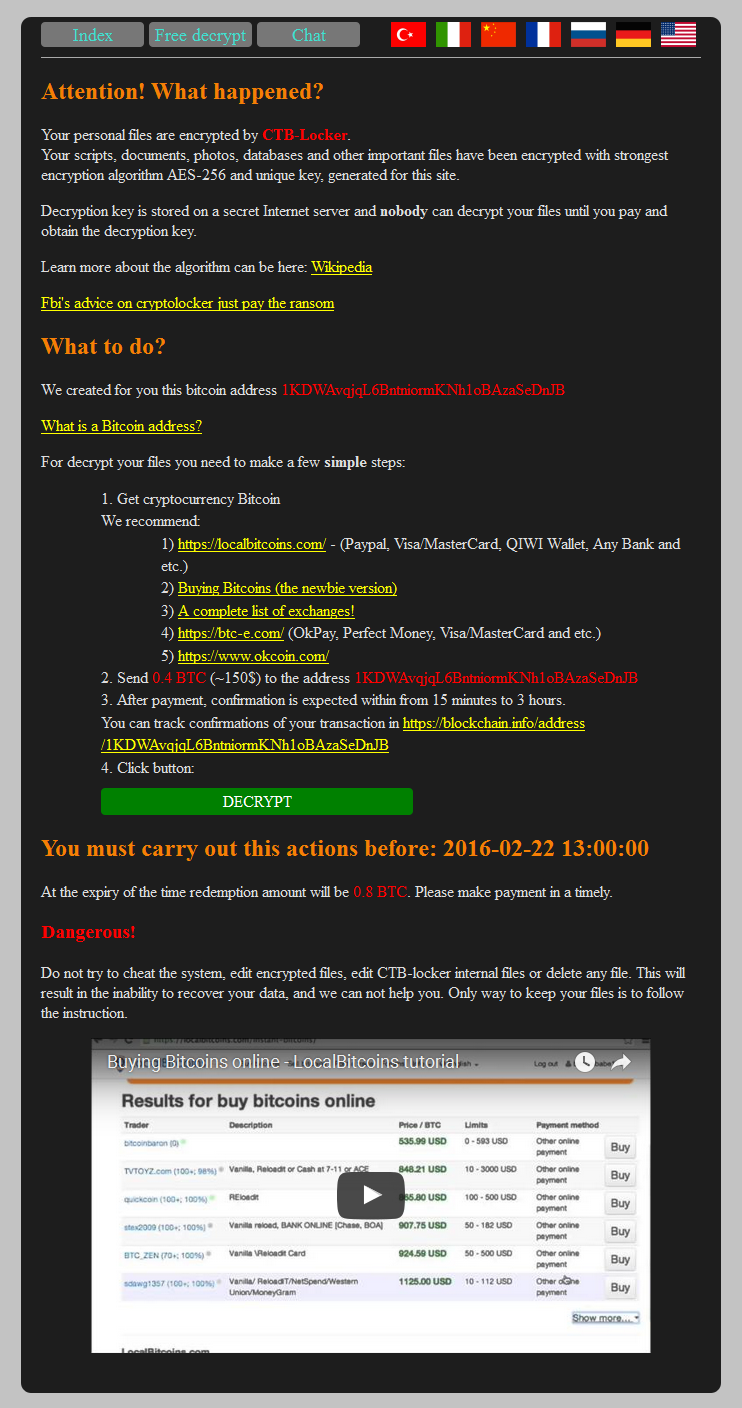
Here’s what a site compromised by CTB-locker looks like: