On April 24th we had a brief interruption on one of our backbone connections that made it appear as if Winhost had dropped off the map.
That interruption, outage, glitch or whatever you want to call it, raised a lot of questions that I thought I could use this opportunity to answer.
Every data center is connected to the Internet through high capacity connections called backbone connections. The “backbone” of the Internet is a group of high capacity providers called tier 1 providers.
Tier 1 providers are pretty reliable, they have to be or the Internet wouldn’t work. But they still have problems from time to time. A cut fiber on a construction site, a natural disaster or power outage, someone flipping the wrong switch – all of these things can cause an outage on a backbone connection.
We do. We have two backbone connections to our servers, provided by different companies. Normally the traffic in and out of the servers is balanced between those two connections using a number of network analyzing tools and a lot of routers and switches.
So if one connection is dropped, everyone whose traffic has been routed through that connection is cut off. The other half of the traffic, coming in on the other backbone connection, doesn’t experience a problem. That’s what happened on the 24th.
If there was an extended outage on one of the connections we could switch all traffic to the working connection. Making that switch (and then switching back when the problem is solved) is not a trivial matter though, so we wouldn’t do it unless we anticipated a long outage on the connection that was down.
A long outage on a backbone connection is rare though, so rerouting all the traffic is usually unnecessary.
Anyone affected by the outage wouldn’t be able to see our site or the forum, since they can’t access anything on our network.
We reacted and responded on Google Plus, Twitter and Facebook, which is probably more effective than an outage post somewhere on our site or on a status site somewhere (that no one knows how to get to).
Things like this are part and parcel of life on the Internet. Any provider who tells you they can host your site and there will never be an outage of any kind isn’t telling you the truth. All of these things (even the mighty, mystical cloud) run on hardware. And hardware is just machines and machines don’t run perpetually without problems.
When they invent machines that do run forever without problems, we’ll be first in line to buy them. I can guarantee that. 😉
Until then, we’ll continue to provide the best service your money can buy, and be open and honest about actual and potential problems.
Thousands of WordPress sites are being compromised causing havoc with their site owners and their hosting providers. The method which the hackers are using is an old method known as a Brute Force Attack. This method simply employs the process of submitting passwords until you finally happen across the right one.
The effects on the site can vary, but it will entail a slower WordPress site, and high bandwidth consumption. This will mean you may pay more for the additional bandwidth you consume even if it was caused by your WordPress site being hacked.
To counter this you need to take two basic steps.
If you want to read up on picking a good strong password, I suggest this Microsoft article that explains how to decide what a strong password entails.
An optional feature worth considering is to enable your WordPress site with the WordPress 2 Step Authentication. It is an added security on top of inputting your login and password credentials with a random generated verification code from Google Authenticator App. You can get more details on how to enable this for your WordPress site on this link. http://en.blog.wordpress.com/2013/04/05/two-step-authentication/
If you want to read up more on these recent attacks to WordPress web sites, try looking at these links.
http://www.bbc.co.uk/news/technology-22152296
Did you know that Mozilla Firefox and Google Chrome like to display your passwords in plain text? No? Well, they sure do.
If you want to see what I’m talking about, follow the steps below.
Open Firefox.
Click on the Firefox Menu at the top left corner.
Select Options, then click on Options.
Click on the Security tab at the top.
Click the Saved Passwords… button. This will open up the Saved Passwords box. Now click on Show Passwords Button.
Example Below:
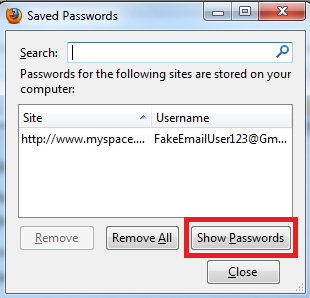
Surprise!
Did your jaw just hit the floor? I know mine did the first time I saw what Firefox was hiding from me all this time.
Now let’s open up Google Chrome and click Settings.
Once you get into your settings, scroll all the way to the bottom and click on Show advance settings…
Look for the section Passwords and forms and click the Manage saved passwords link.
Select the site where you saved your password and click Show button.
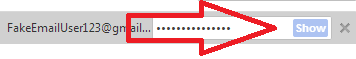
Okay, I’m done with the surprises.
So how did Firefox and Google Chrome get my passwords in the first place?
To get the answer you must also answer this question: Have you ever seen the following notification in your web browser?
Mozilla Firefox:
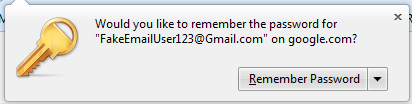
Google Chrome:
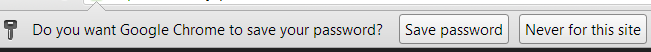
Whenever you clicked on the shiny button “Remember Password” in Firefox or “Save Password” in Chrome, the site username and password are saved within the web browser – and as you also saw – displayed in plain simple text.
Anyone can walk up to your computer and take a quick look at your web browsers history/settings. Just imagine you’re at the office and you step away from your computer and a nosy/curious coworker gets the chance to take a look. That is why it’s important to always lock down your computer before you step away from your desk.
Additionally, say you’re unlucky enough to have some malicious software installed on your computer which happens to allow the hacker gain remote control of your desktop. The hacker will only have to wait until you are away from your computer to check your saved passwords.
What if you sent your computer out to a repair shop and they “just happened to” take a look at your saved passwords? It only takes a few seconds for them to snoop around on your computer and do who-knows-what with your credentials. There are a lot of different ways these passwords can be intercepted. This just happens to be one method of interception that can be avoided.
So what’s the work-around and how do I keep my passwords safe? Fortunately there are plenty of third party plug-ins people use with their web browsers. Perhaps you can recommend what plug-in works best for you in the comment section below.
I found a plugin called LastPass. With 254,540 users and 827 reviews just for the Firefox plugin alone seems to be a great alternative. Best thing about this plugin is that it also works with the Google Chrome web browser.
You may remember that last year around this time we reported that we placed fourth in the DevProConnections Community Choice Awards.
Well I’m proud to announce that this year we placed – fourth!
Again.
And just like last year, we’ll take it, since the top three are the same behemoths that eclipsed us last year (Amazon, GoDaddy and DiscountASP.NET).
We feel pretty good about placing above Rackspace, another monster host that could lose more customers than we have and not even notice it.
But next year – you’ll see – we’re going to crack that top three!
We’re working hard on some cool new stuff (if I tell you about it now, they’ll fire me), but suffice it to say that we’re always working to make Winhost the world’s best hosting platform, and the kind of place where your sites can be proud to live.
Here’s to fourth place, and nipping at the heels of the giants!
If you’re reading this it’s likely that your email account was recently hacked and now you’re wondering how it happened, why it happened to you. Or maybe you’re just wondering how you can prevent it from happening to you.
Let me start off by saying that there are many different ways an email account can be compromised. In this article I’ll cover three of those methods.
Also note that these aren’t the only way an email account can get compromised. People are always inventing new ways of compromising an email account/system. So by the time you finish reading this article, it’s likely that they will have come up with a few new techniques.
Now lets imagine you’re at the local coffee shop sipping on some hot coffee. You open your laptop and connect to the coffee shop’s WiFi. Why not, it’s free Internet, right?
Now it’s time to check your email messages because you are expecting important news. You open the email client on your computer and start browsing the Internet for, you know, important stuff. An hour passes by and you go on your way to work, home, or school. But did you notice the person sitting across from you with their laptop? He just took your email credentials while you weren’t looking. But how did it happen?
Did it happen while you were in the bathroom?
No.
Did it happen when you went for yet another cup of joe?
Nope.
So how did that person steal your email information with out even coming close to your computer?
 Ever heard of a Man in the Middle attack? To put a MITM attack in simplest terms, some malicious so and so sets up their computer to act like a router and tricks your computer into thinking that the computer actually is the router. Then the router thinks the shady computer – in the middle of the connection – is your computer.
Ever heard of a Man in the Middle attack? To put a MITM attack in simplest terms, some malicious so and so sets up their computer to act like a router and tricks your computer into thinking that the computer actually is the router. Then the router thinks the shady computer – in the middle of the connection – is your computer.
Think of it as someone tapping into your network connection. Once this starts happening they can view all kinds of fun packets coming from your computer to the mail server (or to any server). Each time you make a connection to the mail server you are sending your authentication credentials through the bad guy’s computer.
From there it’s easy to use a program to filter out all packets containing login credentials. This includes your Facebook, Twitter, and bank account login information as well. Everything.
So does that mean it would be better to just stay away from your local coffee shop?
Hey, no need to be drastic! You can still go and you can still surf the Internet but it may be best if you didn’t use the coffee shop’s Internet connection. Personally, I don’t trust any network that I don’t own or control.
A nice work-around would be to use the Internet connection on your smart phone. Most smart phones have the capability of turning into a password protected Wifi “hot spot.” They also have the capability to tether the smart phone to your laptop. But, of course you will be using your phone service provider’s data plan.
So if I protect myself from that shady “man in the middle,” I’m safe, right?
Not exactly.
Another way your email account could be compromised is with a virus/malware being installed on your computer without your knowledge. This method is the most common and likely way that your email account (and everything else on your computer) can be compromised. I’ve seen what some of these viruses and malware are capable of doing, and it’s scary stuff.
Some of the virus/malware infections come with a nice little tool called a keylogger. What it basically does it logs all your key strokes and sends them to a server controlled by whoever infected your computer with the virus/malware. So any time you enter a username and password, the keystrokes are logged before the login request is sent. It doesn’t matter that the connection from your computer to the mail server is encrypted.
So how did this software get onto your system, or how can you prevent it from being installed on your system?
You can start by practicing the following:
The third way an email account can be compromised is by social engineering. Some email systems come with a nifty “Forgot your password?” tool. So what’s the big deal about this feature? Well, when you were setting up your email account you weren’t thinking twice and just answered the security questions truthfully. For example the signup form has the following questions:
You had to pick two of them and answered the two question correctly. No harm done right?
Wrong. The question/answer that you’ve set up with your email account should actually be considered to be your second and third passwords. Why? Because the correct answers to these questions gains access to the email account.
It would be best to answer these questions kind of incorrectly. So, let’s say you chose Which street did grow up on? and What is your mother’s maiden name? and answer to the first question is Main St. and the answer to the next question is Smith.
Instead of using the correct answers, you can add a extra character befor the real answer. For example @Main St. and @Smith. If the system doesn’t allow these type of characters then you can also use a letter before the real answer. For example: QMain St. and QSmith . That way if the malicious person finds out the real information, they will still have a hard time getting into your email account.
You must be wondering how these people even get the information in order to gain access to your email account using the security questions method. The answer is very easy. In this day and age most of us use social media sites Facebook, Twitter, YouTube etc. What’s the problem with social media? Well, the problem is we like to give out to much information.
We all like to share share share. Sometimes we don’t realize it, but we give out too much information. So much information that it makes it easy for a malicious person to gain access to your email account using the security question method.
If you keep these things in mind and think about security in new ways, you will protect yourself from a lot of potential headaches.
We showed you The Internet as it was in 1996, but are you ready for the Internet circa 1969?
They were surprisingly accurate in their predictions (even if the film does suffer from mid-century gender stereotypes).
All of us have experienced spam. Spam is unsolicited and unwanted email that arrives in our inboxes. It can range from a minor annoyance to complete disruption of email accounts, or worse yet, can harbor malware, trojans, and viruses.
Some of us go through a period of time where we do not get spam in our inbox, then are suddenly bombarded with it. Some of us even incorporate spam/content filters, often decreasing unwanted and unsolicited email, only to have a renewed surge of spam activity within a year or so.
While our first instinct may be to contact our email administrators to inform them of increased activity and find out if any email server settings have been modified, let’s not forget our own responsibilities to help prevent, diminish, and combat spam from infiltrating our email accounts.
I want to bring up four points that we all need to think about when we want to protect ourselves from these disruptive and intrusive emails.
First, whenever possible, try to avoid using your primary email address when filling out forms. We see it all the time, at the mall or shopping center a booth is offering a free entry to win a prize. We eagerly fill out all the information to win that car or vacation to the Bahamas, and one of the pieces of information they ask for is our email address.
For things like these, try to use an email address that is not your primary email address. Set up a Yahoo or Gmail account that is used solely for these events, and it will help to greatly reduce the amount of spam that arrives in your inbox.
You might think that creating an alternative email address on your primary email domain will solve the problem. For example, your primary email account is [email protected], and you create [email protected]. The problem with this method is that you are disclosing your email domain, and spammers can now bombard @domain.com with “guessed” addresses (such as info@, webmaster@, or even entire dictionaries of usernames) which can eventually spill over to your primary email address.
Second, look at this one as a duty or responsibility: never respond to spam! Delete it, and whenever possible, mark it as spam in your email system so that you build a reputation for what is and isn’t spam. The next time you get a similar spam message it will automatically drop it in your “Trash” or “Junk” folder.
In SmarterMail, if you see an email in your inbox that is spam you can go to Actions/Mark/spam. The more you use this, the more you build up your definition of potential spam.
The third good practice is setting up account level spam and content filtering rules. Many email systems have this feature. In SmarterMail you can go to Settings/Filtering. There you can define your own content filtering and spam filtering rules.
Don’t forget Greylisting! When an email network “greylists” messages, they do not accept the initial incoming message, but rather instruct the sending mail server to try to delivery again later (which most servers will do every few minutes). The assumption being that spam servers will not attempt to send the message again, but legitimate servers will. Greylisting will delay legitimate emails though, so it’s up to you to decide to enable or disable this feature. For the most part, Greylisting is a valuable tool in helping keep your email account clean of unsolicited emails.
Finally, if at all possible, try to avoid “catch-all” email accounts. Catch-all accounts will allow any email address to come through. For example, if you have Catch-all enabled, email addresses that do not exist ([email protected], [email protected]) will make it into your inbox. There may be a business need to have this activated, but this will greatly increase the likelihood of receiving spam, even with a strong spam filtering system.
The last thing that I would like to mention is the necessity of remaining diligent.
Many of us successfully implement the above practices, reducing or even eliminating spam from getting into our inboxes, only to relax our guard, even temporarily, exposing us to a new series of attacks on our email.
Keep in mind that spam is an ongoing threat, and that spam is adaptive and always evolving. Spammers know that they have to constantly update their procedures and techniques to get through to the greatest number of people.
One of the biggest mistakes that we can make is believing that once we have effective anti-spam measures in place, that we do not have to revisit and update those measures. If that were true, spam would have been eliminated a long time ago.
As spammers find new and more sophisticated ways to infiltrate your inbox, you have to remain vigilant and active in combating spam.
Sitting here this morning, as I run through my daily routines of reviewing sales emails, marketing proposals, SEO reports, and general news, I ran across something that made me stop and pause for a good minute. It was a talk by Steve Jobs from 1983.
This was pre-Macintosh Steve Jobs. This was still the bright eyed Steve Jobs that had yet to be “removed from his managerial duties” by the board of his own company only to come back as it’s long lost savior almost a decade later. A Steve Jobs that had yet to earn the labels of “Futurist” or “Visionary.” This was just Steve Job, a 28 year old kid talking to design conference… yes a design conference.
See, even back in 1983 Jobs saw that design was something that needed to be given equal attention when working with technology. It seems something obvious now, but if you think about technology in 1983, design was the last thing on anyone’s mind. PC computers were large briefcase size things that were gray or tan in color.
Even in his talk Steve Jobs says “If you’ve looked at computers, they look like garbage. All the great product designers are off designing automobiles or they’re off designing buildings. But, hardly any of them are off designing computers.” Even in 1983 Steve was looking to change that.
After giving this a listen, I started thinking about 1983. I was 7 years old and already playing with my Dad’s new Commodore 64 typing out BASIC commands to play a game. And after some digging back, I noticed that 1983 was a big year for technology and the internet:
So, an argument can be made that 1983 was a hallmark year for technology and the internet as we know it today. But yet, with personal computing and the internet still in their infancies, Jobs could see what was about to come and where these things could lead.
Listening to the full talk, plus Q&A after, you can hear Jobs talk about ideas and concepts that can be traced forward 25 years later into truths about how we use technology today and every day products like tablet computers. At the end of the Q&A, Jobs even addresses language and voice recognition, which has only now been adopted by the general public with Siri.
So as I’m typing this we have reached the 1 year anniversary, if you will, of Steve Jobs’ passing. For all his flaws (and there were many) it is hard to deny his ability to see past technical limitations and look forward to what he knew was possible.
I was never an “Apple Fan Boy” growing up. In fact I hated Macintosh computers with a passion all through High School and College only using them when all other options had failed. But I did respect how Jobs saw the world in his eyes and was able to rally people around that vision. Listening to this talk only adds to that respect.