It used to be that unless your site accepted payments for products or services, you didn’t really need to concern yourself with an SSL certificate, which allows you to encrypt and secure your site traffic using the https protocol. Those days are quickly coming to an end as web security becomes a larger issue, and giants like Google are making an aggressive push to encrypt all web traffic.
Maybe you have even already received a warning email from Google: “Beginning in January 2017, Chrome (version 56 and later) will mark pages that collect passwords or credit card details as ‘Not Secure’ unless the pages are served over HTTPS.” But what does that mean?
Right now (December, 2016) Chrome shows an “information” icon on all non-https pages (Firefox also uses a similar icon):
Which seems pretty benign, unless you click that icon and get the insecure site warning:
Starting in January of 2017 Chrome is going to take that a step further and add a text warning:
Then “eventually” – which, knowing Google, could be any time – they are going to throw the red flag at non-https pages:
At the moment those warnings only apply to http pages containing password or credit card input fields, but Google definitely plans to extend the Chrome warnings to all http pages, regardless of whether they accept user credit card or authentication input.
Using https encrypts connections to prevent anyone from tapping in to the communication between your website and your visitor’s browsers. It also prevents the bad guys from exploiting your site by injecting malicious code or unwanted advertising into your user’s browser.
The https connection lets your visitors know that they’re securely connected to your site. That what they’re seeing is legitimate information. It also prevents anyone from accumulating of a lot of user data or behavior related to your site traffic. Aggregate data like that can be used for a number of malicious purposes, so blocking access to it is a good thing.
Right about now you may be thinking, “Okay, I get it, but I’m not really concerned about someone listening in to my site traffic.” That’s understandable. Most sites run a pretty low risk of being targeted in that way. But you probably don’t want to see every page of your site displaying a red “Not secure” warning in Chrome (and eventually in other browsers as well).
That’s reason enough to take steps now to make every page of your site available via https (and redirect http requests to https). You might even consider it a priority, since the Chrome browser currently has a 56% market share, and that percentage is increasing.
But aside from avoiding the warning label, there can be other benefits to using https. In their own words:
“Google uses HTTPS as a positive ranking signal. This signal is one amongst many others, and currently carries less weight than high-quality site content; you should not expect a major SEO advantage for moving to HTTPS in the short term. In the longer term, Google may increase the strength of the HTTPS boost.”
Google is making it pretty clear that in the future they are going to give an edge in search result rankings to sites that use https. And who doesn’t want an edge where that’s concerned?
The good news is it isn’t exactly a “move.” Your site stays on the same server, you just add an SSL certificate to your account and make the necessary changes to redirect http traffic to https. This article is already pretty long, so we won’t do a tutorial here, but other than redirecting to https, there are a few other things you’ll want to watch out for:
If you use Google Webmaster Tools, after you’ve made the switch, add the https version of your URL as a new property, set the “preferred version” of that property to https and (re)submit your sitemap. Here’s a Google-centric FAQ on transitioning to https that you may also want to take a look at.
Finally, you may have heard that you can get a free SSL certificate from Let’s Encrypt. That’s true, and you can use those certs here at Winhost. But the Let’s Encrypt certificates come with some drawbacks. Make sure you’re aware of what’s involved in using such a cert before you commit to one.
We’ll have more information on this subject in the coming months. We expect that there will be a lot of questions when Google makes the changes to Chrome, and we’ll do our best to address those questions here and in our Knowledge Base.
The changes have already begun in the latest version of Chrome (55.x). They aren’t flagging insecure sites yet, but they are spelling out “Secure” now:
There is a lot of talk around using https “everywhere” these days, even on websites that do not do any financial transactions or accept user data input. Google already uses https as a factor in search results (though it’s a small factor, and not universally used in results everywhere in the world). But they have made it clear that their intention is to expand the use of https as a search results ranking factor next year.
All of which has a lot of people who may have never considered using an SSL certificate before looking in to making the move to SSL/https. The main barrier for a lot of people isn’t the technical issues around implementing an SSL certificate, but rather the price. SSL certificates cost money. Some of them (like those with “Extended Validation”) cost a considerable amount of money.
A group of security-minded people thought there should be a free alternative, so they got together and the open source Let’s Encrypt project was started (by the Internet Security Research Group, with support from the Electronic Frontier Foundation, the Mozilla Foundation, Akamai, and Cisco Systems). Let’s Encrypt is now up and running, issuing free SSL certificates to anyone who wants one.
Pretty great, right? Well, yes and no.

For instance, if you want one of those Extended Validation certificates, you can’t get it from Let’s Encrypt. Organization Validation, Extended Validation and wildcard certificates are not available. Let’s Encrypt does not verify sites, so if you want a security “seal” to put on your site or order form, you can’t get it from Let’s Encrypt.
That’s right, Let’s Encrypt does not verify sites, which means hackers are building malicious sites using Let’s Encrypt certificates because they’re free and the bad guys can remain anonymous. Wait a minute, though – isn’t validation the whole reason for a security certificate in the first place? And what will become of the Let’s Encrypt certificates if their system becomes overrun with malware and phishing sites?
Even if you don’t care about any of those things, the Let’s Encrypt certificates have a major convenience drawback, because the certificates are only valid for 90 days. That means that every three months you have to request a new Let’s Encrypt certificate and install it on the server, and that process is no fun. Especially on Windows servers (like those at Winhost), since there is not any server-side automation available.
But increasing security is never a bad thing. And don’t forget, Google is going to look more favorably on https sites very soon, so an SSL certificate should be on your to-do list, no matter what kind of site you run. If you want to use Let’s Encrypt on your Winhost site, you certainly can. We support it. We don’t recommend it – for the reasons we just mentioned – but if you’re up for going through the process every 90 days, you can.
But if you’re more of a set-it-and-forget it type, we offer a full range of SSL certificates, starting at as little as $39 a year. You can register a certificate for two years as well, meaning it’s not something you have to think about every 90 days, or even every year. If you want to secure your site (and don’t want to see your Google ranking drop) you may want to get yourself an SSL certificate soon.
![]()
As if everything related to domain name registration and maintenance wasn’t already screwy enough, there is a new change on the horizon that promises to make updating your domain names even screwier.
After December 1, 2016, when you change the first name, last name, contact email or organization field for your domain, it will trigger something called the “trade process.” Without going into too much technical detail, what that means is those previously minor ownership information changes will now be treated the same way a domain transfer is treated.
The problem with that is now the domain owner will have to approve those changes via two separate – but similar – emails. That’s because the “current” and “previous” owner – which are the same person in this case – need to explicitly approve the change, or it will not be made.
So if you update your name or the name of your organization, you’ll have to approve that change in two emails. If you update the email address associated with a domain name, you’ll have to approve that change at the old and the new email address. You can probably already see some potential problems, can’t you.
So why are these changes happening? Well, ICANN started reviewing the transfer process almost 10 years ago, when potential issues with the existing transfer policies were identified. So they began looking at “special provisions” for change of registrant during a transfer in order to prevent domain hijacking.
Which sounds like a good thing, but now, a decade later, what we ended up with is a process that may make it slightly more difficult to hijack a domain, but definitely makes a lot of day-to-day maintenance tasks more difficult and confusing.
Every registrar has some leeway in how they implement the changes, so we’re not sure yet exactly how it’s going to work for domains registered through Winhost. We’ll do everything we can to keep the confusion to a minimum, and we’ll post an update here when we have more information on how things shake out.
Do you know what ransomware is? It’s a computer compromise, typically spread via a macro in a Microsoft Word file. Those spam “invoices” you get, with a .doc attachment? They’re almost always ransomware. If the macro is run, most of the document and image files on your computer are encrypted, and the hacker then extorts money out of you to get the key. The longer you wait, the higher the price.
Right about now you’re probably thinking, “Not a problem for me, I have backups for all my important files!” Which is good. You can reformat your computer, restore your backups and be done with it. Lesson learned. If you’re not backing up your computer files, now’s the time to start, right? Right? Get started. Seriously.
If that wasn’t bad enough, the people who write ransomware have now figured out how to encrypt your website files and hold them for ransom, and compromises are spreading rapidly across the web. The compromise is done through vulnerabilities in third party applications or your own scripting (out-of-date WordPress sites are a common target – update your WordPress site, plugins and themes!).
At the time we’re writing this, that ransom starts at around $175, and goes up from there the longer you wait. The best way to guard against that is the same way you’ve guarded against site compromise forever: keep your third party application updated, and examine your own code for vulnerabilities.
But if the bad guys do get in and your site files are encrypted and held for ransom, what can you do?
Well, we make site and database backups every day, so we may be able to help you restore the unencrypted version of your files. But our backups are meant for disaster recovery, so there’s often a fee involved with pulling and restoring a copy, and it will take a little time. In addition to that, we only keep a few days of backups. If you don’t notice a ransomware compromise for four or five days, all of our backups will probably be copies of the compromised files, and therefore not useful in restoring the site.
The best answer is maintaining a tight ship, as far as your site is concerned. But a really good standby strategy is our SiteBackup service. It allows you not only to back up website and database files, but to keep multiple versions of those backups for long periods of time. That increases the likelihood that you will have a “clean” backup to restore to defeat the ransomware goons. The best part is you control the backups, they’re available to you immediately any time you need them.
Another cool thing that SiteBackup can do is alert you if Google flags your site as compromised, and automatically disable any further backups. That means you can rest easy that you’ll always have a clean backup for restoration.
Any way you slice it, it’s better to be safe than sorry, so we really recommend checking out SiteBackup. It’s inexpensive (starting at $2.95 a month for 10GB of backup space!), extremely easy to use, and – we think – some of the best peace of mind money can buy.
Activate SiteBackup in Control Panel now.
Here’s what a site compromised by CTB-locker looks like:
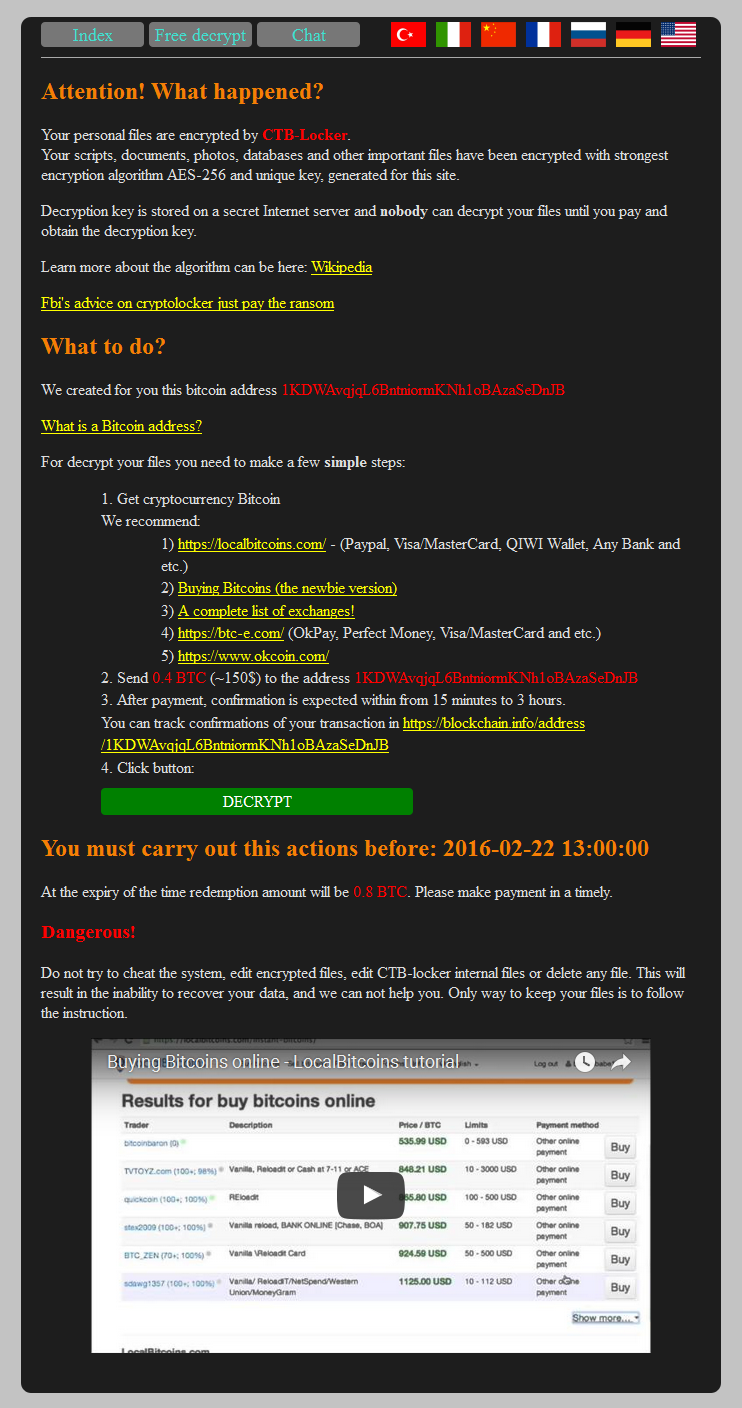
![]()
Note: beginning with Chrome version 46 the yellow caution triangle has been removed from the https URL when Chrome encounters minor errors such as those described in this article.
If you use an SSL certificate (https) on your site, you may have seen a couple of new things happening in Google Chrome.
When you upgrade the Google Chrome browser to version 41 or later, you may see various warning messages such as, “The identity of this website has not been verified,” “Your connection to <domain> is not encrypted,” or other visual indications that the https connection is not secure.
Those indications can appear when your SSL certificate uses a SHA-1 signature (most SSL certificates issued before 2015 use SHA-1).
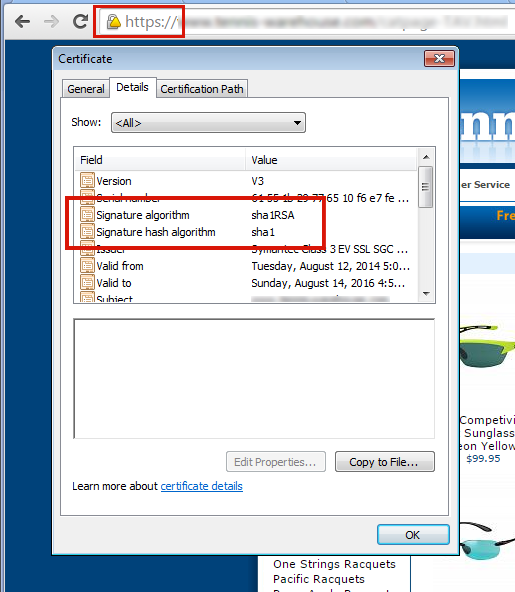
To fix the problem of browser security warnings you must get your SSL certificate re-keyed for SHA-2. If you don’t see those warnings in Chrome and you purchased your certificate recently, it may already be SHA-2. You can verify using this test site.
1) Contact us and we will re-generate and re-submit the CSR.
2) You’ll then get an email from GeoTrust with a link to complete the process. When completing the re-key on the GeoTrust site, be sure that SHA-2 is selected as the “Hashtag Algorithm.” You can find step-by-step instructions (and a video) here.
3) After you’ve completed the reissuing process, you’ll receive an email with the new certificate. Go to Control Panel and paste the new certificate into the SSL manager and you’re finished.
1) Contact us and we will re-generate the CSR and email it to you. Then you’ll have to contact the issuer of your certificate to get your certificate re-keyed for SHA-2.
2) When you receive the re-keyed certificate, go to Control Panel and paste the new certificate into the SSL manager and you’re finished.
There is another potential problem after you’ve re-keyed your SSL certificate. While the address bar will show the green lock icon, if visitors dig deeper in Chrome, they may see an “Obsolete Cryptography” message.
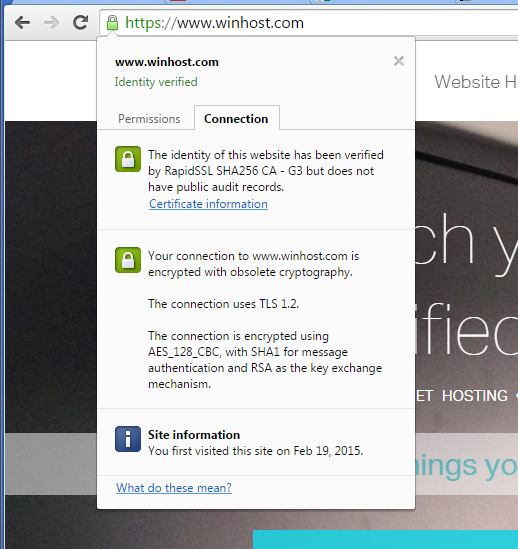
Basically what’s happening now is they are ignoring the cipher preference we use on the server (which includes their preferred ciphers) and pointing out any “weak ciphers” they find. You might notice that many large corporate sites (such as Apple) are also insecure according to Chrome, for similar reasons.
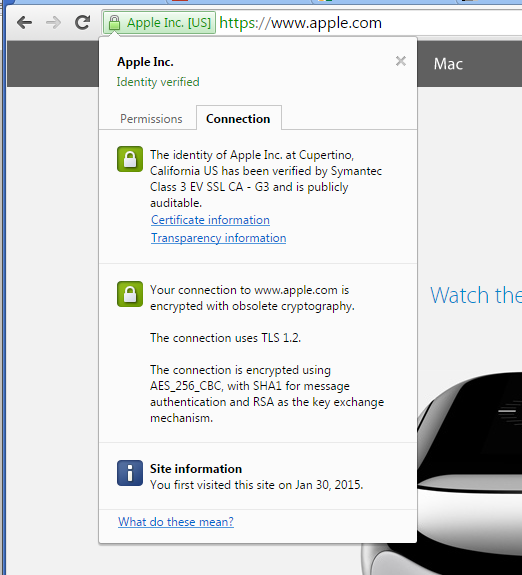
That “obsolete cryptography” message may be with us for a while because Google is not providing any information (yet) on exactly what they want from the server to stop calling it insecure. It would seem that what Google would like to see is every server everywhere removing support for all older cryptographic methods.
The problem with that is removing some of those methods will shut out visitors using some older browsers and operating systems that don’t support newer methods (i.e. Windows XP). Since our servers are shared by many customers, it isn’t really an option for us to make global changes that prevent some visitors – even a small number – from accessing our customer’s sites.
We do run some special servers that do not support any of the older cryptography methods, they are primarily used by customers who need a “hardened” server to pass a PCI compliance scan. But the added security comes at a cost, as older browsers can’t connect to sites on those servers via https. Additionally, a few other things that you may take for granted now may not work, or may require adjustment or a work-around on your part. But if you’d like to move your site to such a server, just let us know.
And of course we continue to monitor information from Google on recommended server configuration, as well as continuing to test various configurations ourselves to prevent the “obsolete cryptography” message.
If you have any trouble re-keying a certificate, or if you have any questions about these ongoing changes, drop us a line and we’ll do our best to help.
Google announced that they would be closing Google Checkout over a year ago, but now they have announced the date when the service will close permanently; November 11, 2013.
If you use Google Checkout on your site they have a FAQ to help you transition to another system.
One can never underestimate the importance of upkeep and routine maintenance, especially when it comes to web sites and applications. When we do not practice due diligence or neglect our web applications, hackers can find holes, weaknesses, and exploits in our so-called “secure” sites.
That holds even more true when it comes to “canned” applications such as Joomla. We have learned that Joomla version 2.5, and 3.1.x have a security hole that can allow anyone to upload malicious files through your application.
The malicious files can perform cross-site scripting (injecting a string of code to your web pages, which can redirect users to a phishing site), or distribute malware or Trojan files that can affect your visitor’s computers.
The security hole in Joomla is its Media Manager, which offers you a tool to upload files to the website. This is a necessary function in a CMS such as Joomla. Joomla comes with its own filtering mechanism that prevents anyone uploading files with specific extensions that can be malicious in nature. Files with extensions such as .exe or .php should not be uploaded as they can infect your web application.
However, the bug is that a trailing dot on a file name can circumvent the filtering mechanism. Normally Joomla will prevent the upload of files with a .php extension such as document.php. However, include a period at the end, such as document.php., and the file no longer fits the .php criteria.
Nasty bug to say the least. What is more frightening is that you do not have to be a registered user or have administrative privileges to the application to exploit the bug. If the Media Manager was set to be available to the public, anyone can inject your site with a malicious file.
The simplest way to solve this problem is to go to Joomla’s website, download the most recent version, and upgrade. This should have the latest patch to this security threat.
http://joomlacode.org/gf/project/joomla/tracker/?action=TrackerItemEdit&tracker_item_id=31626
http://www.joomla.org/announcements/release-news/5505-joomla-3-1-5-stable-released.html
If an upgrade is not an option for you, you can manually add the code that will prevent users from uploading files to your application with a trailing dot.
Navigate to /Libraries/Joomla/Filesystem and open file.php. Scour the code to find where the makeSafe function starts. Add the line:
// Remove any trailing dots, as those aren’t ever valid file names.
$file = rtrim($file, ‘.’);
If this line already exists then your Joomla application is immune to this specific security hole.
That doesn’t mean that you should not routinely follow up on the most recent news concerning your web applications. To really secure your site it is important to stay informed of the most recent patches for your web application.
Here are links you may want to check to stay up-to-date with Joomla’s security fixes. Keep in mind that some security patches may not apply to you depending on the version you are running.
http://docs.joomla.org/Vulnerable_Extensions_List
Let me lastly say that we here at Winhost take this threat seriously. As of today, we have updated our App Installer to the most recent Joomla version (3.1.5) with the security patch installed. If you installed your Joomla application with this newest release, you are protected from this specific threat, however if you have installed an older version from us you may want to check file.php within Joomla and make sure the appropriate line is added.
War Thunder is a free to play online WWII Air Combat Simulator, developed by Gaijin Entertainment and release for Open Beta in 1 November 2012, this game has quickly consumed my free time. WWII era aviation being one of my personal interests and free-to-play always being a plus, I quickly feel in love with the game.
It has several different game types to choose from, all of them team based, with differing levels of historical accuracy and realism.
You can find out a lot more general information on the game as well as the free download at warthunder.com.
This article focuses on my current favorite plane to fly, the Bell P-39 Aircobra.
Introduced the P-39Q was a solidly constructed craft with an innovative feature of placing the engine mid-ship, under the pilot. This was done in order to make space for the massive 37 MM cannon that sits in front of the pilot and fires through the propeller hub. This was backed up by two nose mounted .50 caliber machine guns and four .30 caliber machine guns in the wings.
While moving the engine back did favorably change the center of gravity for the plane and offer the pilot increased forward visibility it unfortunately placed the engine in a cramped part of the fuselage.
With little room left the design choice was made to forgo a turbo-supercharger for the engine. This one design choice kept the Aircobra from achieving great success and prestige.
Without the turbo-supercharger the plane was restricted to low altitude work less than 5100 meters. This being unfortunate because the slow firing 37 MM cannon was best suited for large and slow targets, like the high altitude bombers of the 3rd Reich.
Unable to engage in high altitude air combat or perform bomber escort duties and only capable of carrying a meager 500 Kg bomb-load the P-39 was not suitable for the war in Europe. Without an arresting hook and with only moderate range and endurance the plane was also not suitable for combat in the Pacific.
It was through the lend-lease program that the Aircobra was able to find its niche.
In the Eastern Front combat took place at much lower altitudes, the lack of a turbo-supercharger was not an issue, Russian pilots had no problems bringing the 37 MM cannon to bear on German ground targets as well as dog fighting with the Fw 190 and Me 109’s of the Luftwaffe.
Being a level 6 plane the Aircobra is the go-to choice for arcade and some historical battle missions for mid-level players. I have access to level 9 planes now and I still include the P-39Q and P-39N in my arcade line-ups and regularly use them in historical battles. The machine gun armament is sufficient to take down other interceptors or single engine attack craft with ease and the 37 MM cannon is absolutely devastating against all aircraft, from smaller planes all the way up to 4 engine heavy bombers. The lack of turbo-super charger is much less of an issue in game than it was in real life, especially in arcade mode. This is because most air combat takes place much lower than 5100 meters, usually below even 2000 meters.
In game the plane is a stable weapons platform, at speeds exceeding 600 KM there is minimal turbulence or jutter, so once you are on-target you will stay there, lining up and putting down targets is a breeze.
The 37 MM gun IS hard to aim correctly against maneuverable opponents, it has a slow rate of fire and the projectiles themselves seem to move a lot slower than standard machine gun bullets, but with a lot of practice and some luck you will find yourself “one-shotting” (one shot fired, one plane downed) in almost every match.
The downside to such a heavy armament is that the P-39 is very fragile.
It does not have an armored cockpit, and the engine being placed in the center of the fuselage means that more shots are likely to hit it.
I often find my control surfaces being completely shot out after just one pass by an enemy fighter.
The lack of armor means that gunners on the bombers you are hunting can disable you in just a burst or two, so care must be taken to always present yourself as a hard-target.
Thankfully due to the responsiveness of the planes controls this is not hard at all.
The Aircobra is by no means or dog fighter or an energy fighter, in any kind of turning match you will find yourself with a bogie on your tail 9 times out of 10.
The plane does not retain speed or energy in a turn, after a 1000 meter dive one turn is all that it takes to reduce your speed from 600 Km to just 300 Km, and this is a death sentence if any of the enemy are around to take advantage of it.
Coupling this with the planes generally weak armor most new pilots will not last long unless proper tactics are employed.
I fly very conservatively.
I like to imagine the pilot in the plane is really me, and dying is the last thing I personally want to do, so I try to do everything in my power to ensure I will come out on top of a fight before committing. In the beginning of a match I will generally take 5 to 10 minutes to gain altitude while flying perpendicular to the enemy.
The advantage of this is 2-fold.
1. The enemy does not get within striking distance of me, and I gain the altitude advantage.
2. My team mates generally rush in and occupy the enemy, allowing me the ability to attack from the side or above.
I generally stop gaining altitude around 5000 meters and then scan the horizon for bombers.
If I see a lone bomber trying to make a pass on our airfield or a remote column of tanks I will pursue it and try to bring it down with my heavy cannon. Bombers with escorts are not a viable target unless I know for sure the escort has high-altitude difficulties as well. Bombers themselves are hard targets to hit, they are fast and will be shooting at you with their gunners, and anything else to worry about, like a Bf 109 escort, will make getting the kill shot with your cannon much harder, if not impossible.
Also, you cannot even dream of dog fighting at this altitude, your plane will take almost half a minute to turn in a circle and your engine will be so choked for air you will be struggling to keep speed.
So let’s say that there are no viable high-altitude bomber targets, what do you do then?
The key to playing as the Aircobra is to realize that you are not in an “honorable” plane, you do not fight the capable members of the enemy team, you look for those in a bad situation, wounded, alone, or a severe positional disadvantage.
Ideally all 3.
While the Aircobra cannot keep energy in a turn it can dive at incredible speed without fear of breaking apart, in arcade i personally have dove as fast 850 Km and in historical battles 700 Km before my plane started to experience any noticeable turbulence. Using this to your advantage you will stay on the edges of a fight, several kilometers above and wait for someone to wander off or try to escape. Then you pounce on them and unleash a massive barrage at high speeds, then after you pass you use as much of your gained speed to gain altitude back up to your vantage point, rinse and repeat.
Some will recognize this tactic and the boom and zoom, this is how you fly an Aircobra.
The P-39 is a ideal fighter for those who don’t mind taking some time to plan a route of attack, its high maximum speed in a dive and fierce armament mean that if deployed carefully no target is out of reach, but it’s lack of armor and poor turning characteristics mean that it cannot be flown without thought.
It is one of my favorite planes for its potential to kill quickly, but it is also one of my frustrating to fly because of its potential to die just as fast.