We were notified by our upstream provider about a recent rise in hacking activities related to older Telerik Web UI Controls that were integrated into older Sitefinity and DotNetNuke applications and may have been used in older custom ASP.NET web applications. Since the warning, we have indeed seen sites hosted at Winhost getting hacked due to this vulnerability, so we wanted to let you know about it.
Some in the security industry are calling this hack Blue Mockingbird and Telerik has even posted about this issue on their blog.
In general, what hackers are doing is using a built-in function of the Telerik Web control – a function that the website may also use – to upload files to the site. Once uploaded, the hacker uses the files to do malicious stuff or the files may just sit there and do nothing (until some future time when the hacker decides to wake it up).
Apparently, there are many different hackers and hacking groups that are exploiting this vulnerability. If the hacker messes up the customer’s website or uploads some phishing site, the customer and/or the host would probably notice and deal with it. But the major issue is that many times the files that are being uploaded are doing nothing – so the site owner doesn’t know something was uploaded to their site and the host won’t know the site got hacked. The hack is clever because its use of the Telerik control looks legitimate.
To deal with this hacking activity, we are monitoring our intrusion prevention system more diligently and made updates to our server security. And our staff are actively looking out for any indication of hacking activities.
Sitefinity and DotNetNuke users
If any customers are running Sitefinity or DotNetNuke, get in contact with our technical support and we can check if your site is vulnerable. If your site is vulnerable, we can discuss next steps in how to deal with it.
Custom Applications Using Telerik Web UI Controls
If you use Telerik Web UI control in your custom ASP.NET web applications, get in contact with our technical support and we can check if your site is vulnerable. if your site is vulnerable, we can discuss next steps in how to deal with it.
If you have any questions or concerns, feel free to contact us.
Visit Winhost to learn more about our Windows hosting solutions

Lately, we have been seeing a higher number of DotNetNuke (DNN) sites getting hacked via a known Telerik.Web.UI.dll vulnerability that’s been around for years. DNN released a patch a few years back. However, we have been seeing in influx of compromised DNN sites caused by this easy-to-fix vulnerability.
If you’re using DNN Versions 5.6.3 through 9.0.1 you must apply this patch to avoid disruptions to your site. More importantly, prevent it from getting hacked.
If you are running a DNN site and need help or want us to patch DNN for you, stop reading and contact our support department. We can help you apply this patch to your site at no cost. Please note that if your DotNetNuke site requires upgrading, then we can help you with that but we do charge for upgrading services.
First thing you need to do is download the patch directly from the DNN Site here: Critical Security Update September 2017
Once you have zip file from the DNN Site, you need to install it as you would an Extension within DNN.
Log into your DNN site as the SuperUser default login.
Navigate to: [HostingAccountDomain.com]/Admin/Extensions
Or look for the Extensions link within your DNN Site.
Click on the Install Extension Wizard button
Select Choose File button and select the zip file you just downloaded from DNN in Step 1 and click Next
If you receive a random 500 or 404 error within your DNN site after clicking Next from Step 5. Please note the following, otherwise move on to Step 6 below.
You most likely received this error because you need to increase your maxRequestLength setting within your web.config file. You can access this file via FTP.
Look for the setting: maxRequestLength=”12288″
And change it to: maxRequestLength=”28000″
The above increases the limit to 28 MB.
Save your changes and upload the updated web.config file into the same directory overwriting the old web.config file.
Then try Step 5a again.
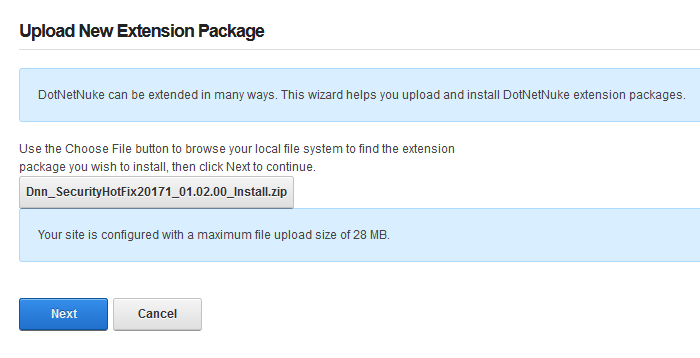
You will see the Package Information about the HotFix. Go ahead and click on Next.
Click Next on the Release Notes window
Read and place a check next to Accept License
Click Next.
You will then see the Package Installation Report. Click on the upper right X to exit out of the window.
Once your extension page is reloaded. You will see the newly installed Patch for your site.
If you are using DNN, make sure to look into this. There are hackers out there that are targeting DNN and we don’t want you to be a victim of their malicious activities.
If you have any questions or concerns, just contact us.
WordPress is one of the most popular applications on the web with over 74 million installations – that’s a staggering 35% of all the active websites! Unfortunately, with its massive install base, it is natural for hackers to focus a lot of attention on hacking WordPress sites.
In this post, I’ll describe the most common attacks and what you can do about it to lessen the probability of being a victim.
In general, we have found that hackers compromise WordPress installations mostly by one of the two following methods:
Hackers operate many bots that worm through sites and test random login and passwords in the WordPress Admin page.
To get an idea of the scale of attempted logins we’ll take a look at some stats from our own infrastructure. At Winhost, we deploy an Intrusion Prevention System (IPS) on the network edge to detect many malicious activities and try to stop hackers before requests hit our servers. We have rules deployed on the IPS system to thwart Brute Force attacks. However, we cannot make the rules too aggressive because then it can block legitimate requests. It’s a delicate balancing game which we tweak constantly.
Based on the statistics of our IPS system, we typically track 9-10 million WordPress login attempts a month (both malicious and legitimate attempts). Check out the plot below.

About 20% of these attempts are blocked by our IPS system.
2. Outdated Plugins / Themes
Many WordPress sites use various plugins and themes to enhance their sites. The problem is that many plugins and themes have security holes that allow hackers to upload malicious files to the server without the need to log in as an administrator. As a result, we constantly see malicious bots testing for these plugins.
What does Winhost recommend to protect your WordPress site from getting hacked?
Credential Security
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<security>
<ipSecurity allowUnlisted="false">
<add ipAddress="1.2.3.4" allowed="true" />
</ipSecurity>
</security>
</system.webServer>
</configuration> PHP Version
Set your site’s PHP version to 7.1 or above
Update WordPress Frequently
Backup Site and Database
We recommend that you backup your site and MySQL database. We recommend you keep at least 2 weeks worth of backup because you may not realize your site is hacked immediately. Don’t rely on Winhost’s nightly backups because it will only store about 3 days worth of backups. You can automate the backups by using our SiteBackup service.
SiteLock Security service
Consider subscribing to SiteLock Premium or Enterprise Service and enable SmartScan. SmartScan will check your site daily for malicious files and also report on newly created files.
What we do at Winhost to protect your WordPress site
Visit Winhost to learn more about our WordPress Hosting solution


Email is a vital form of communication and many customers have asked us about Email backups. So we are happy to introduce a new service, EmailBackup!
You Can Automatically Backup Any Email Box
You can easily set up automated backups for your email and attachments. You can backup your email from Winhost email servers or virtually any other email boxes you have elsewhere.
It’s Secure
The email backup storage is secure and encrypted and is also secure during transit.
You Can Easily Search and Restore
Tools are available to search your email archive and you can restore any email messages from your backup.
Manage Your Backups In a Separate Control Panel
The EmailBackup portal is a separate control panel from the Winhost Control Panel and lives outside of Winhost infrastructure. So in the event your Winhost Control Panel is down for any reason, you still have access to your Email backup storage.
A Very Cost-Effective Solution
EmailBackup starts at $1 per month. Peace of mind for less than a cup of coffee! And to sweeten the deal even more, we are offering EmailBackup for 30 days FREE so you can test it out without any risk.
Get Started with EmailBackup Today
30 Days FREE
Click here for more information about EmailBackup from Winhost
Some customers have asked what is the best way to prevent visitors from accessing certain files on their sites. The solution we generally recommend is what I am going to cover in this article.
First you will need to connect to your site through IIS Manager and the instructions can be found here: https://support.winhost.com/kb/a628/using-the-microsoft-iis-manager.aspx
Once you have made a successful connection you should get a screen that looks like the one below:
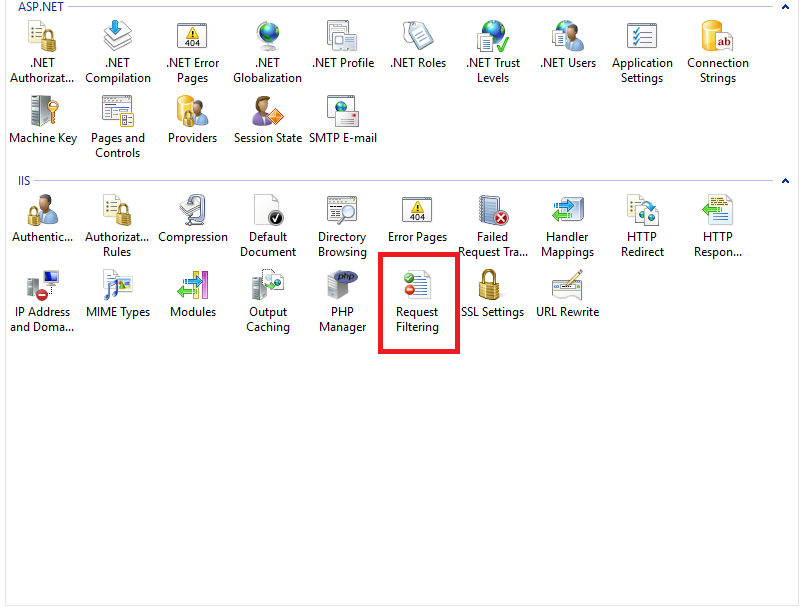
Double click on the highlighted (red box) “Request Filtering” option. On the next screen, navigate to the “Hidden Segments” tab.
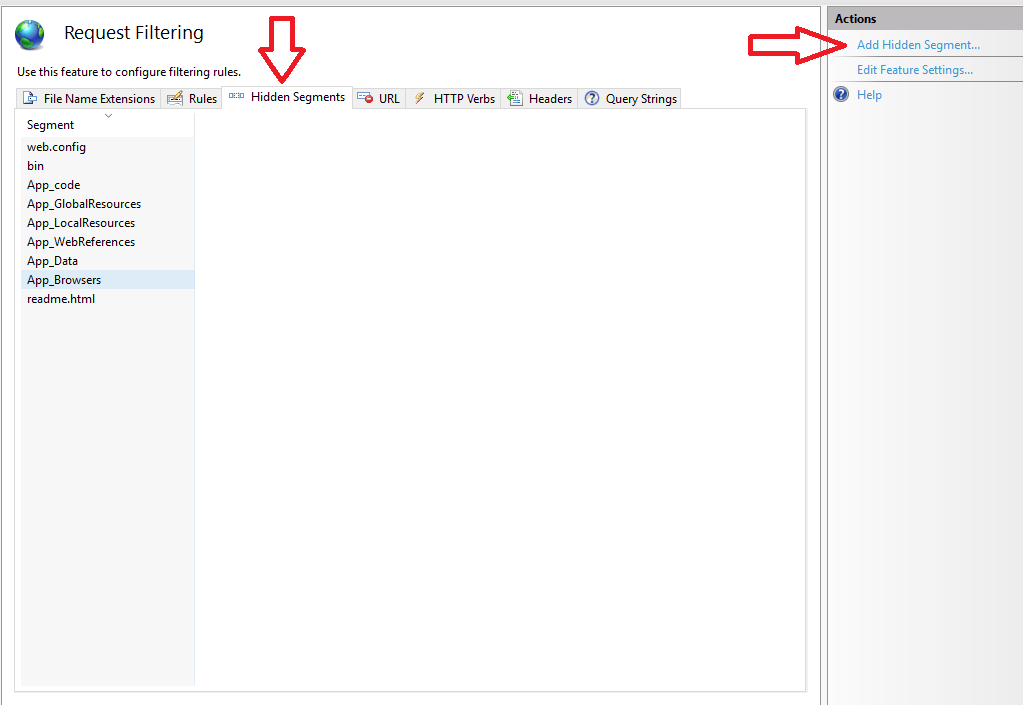
This screen will probably list some default files that are blocked. We will add the file from our site that we don’t want visitors to access. To do this, click on “Add Hidden Segment” and type in the filename you want to deny access.
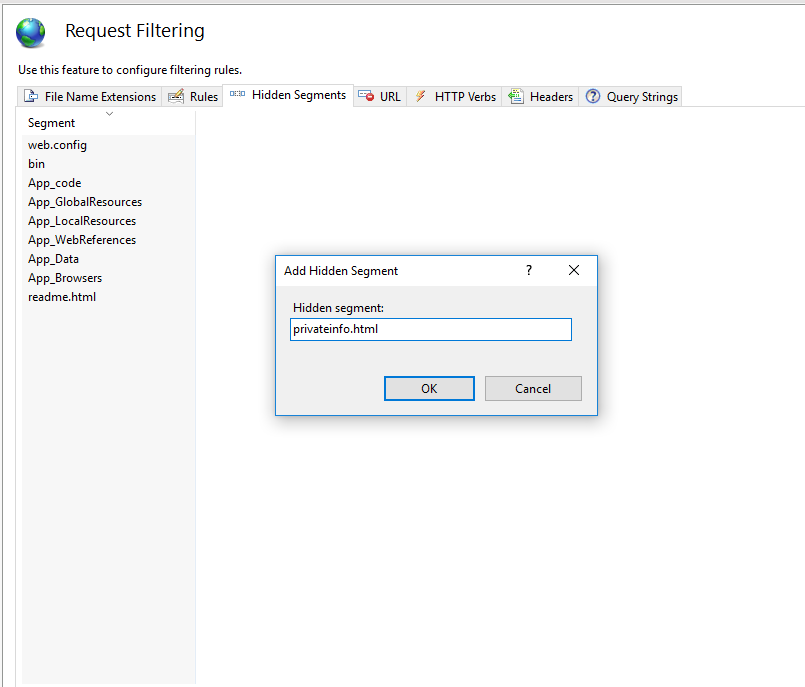
And that’s all there is to it. Now when someone tries to navigate to that file they will get the error demonstrated below.
Before:
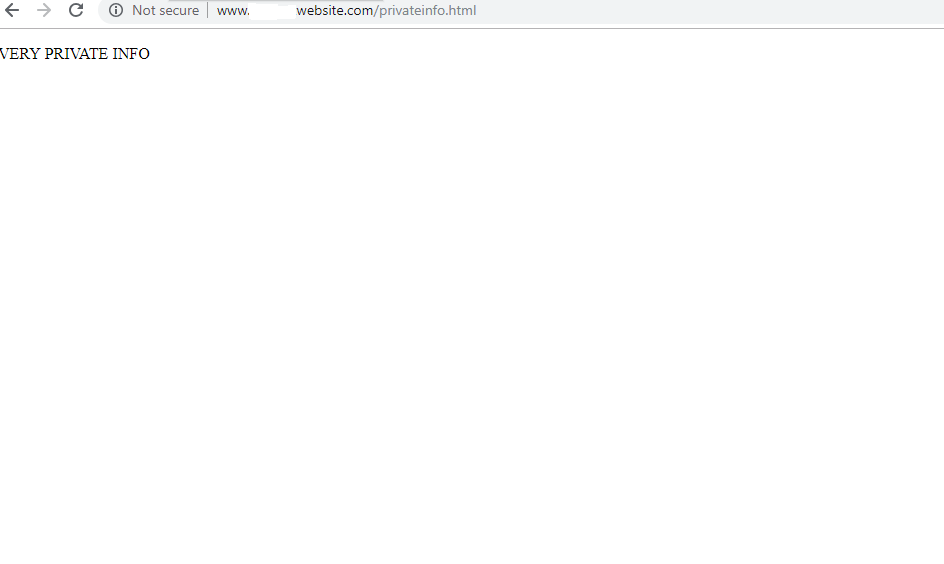
After:
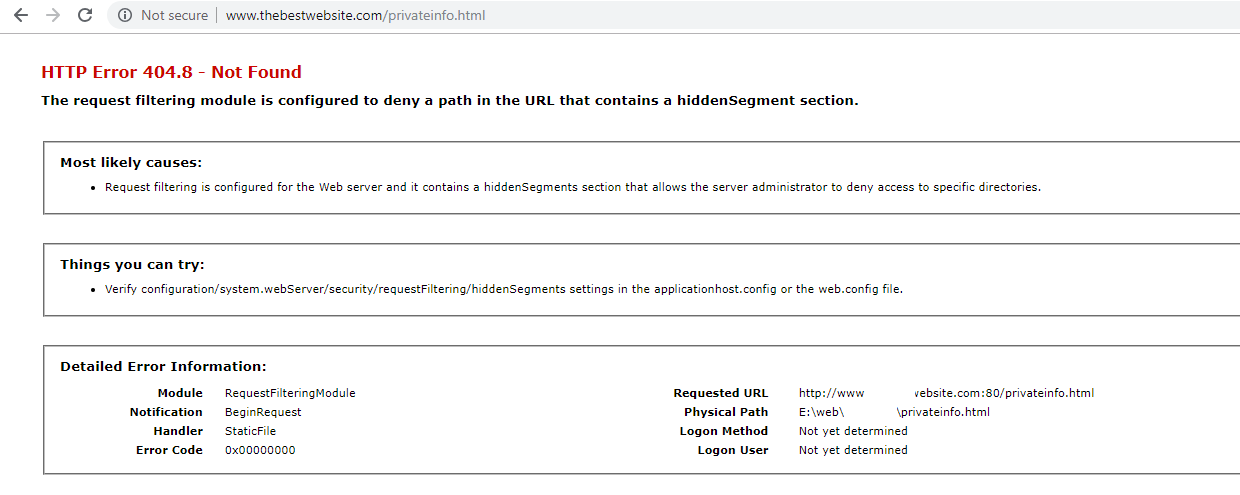
This is how the rule appears in your web.config after created.
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<security>
<requestFiltering>
<hiddenSegments>
<add segment="readme.html" />
<add segment="privateinfo.html" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
</configuration>I hope this helps you protect your site.