![]()
**This article assumes that you have a WordPress site installed at Winhost. If you don’t and want to install WordPress, go to your Winhost control panel and find WordPress under the App Installer.**
To begin you will need to log in to the Admin section of your WordPress site which can be accessed by adding /wp-admin after your domain name such as: HostingAccountDomain.com/wp-admin
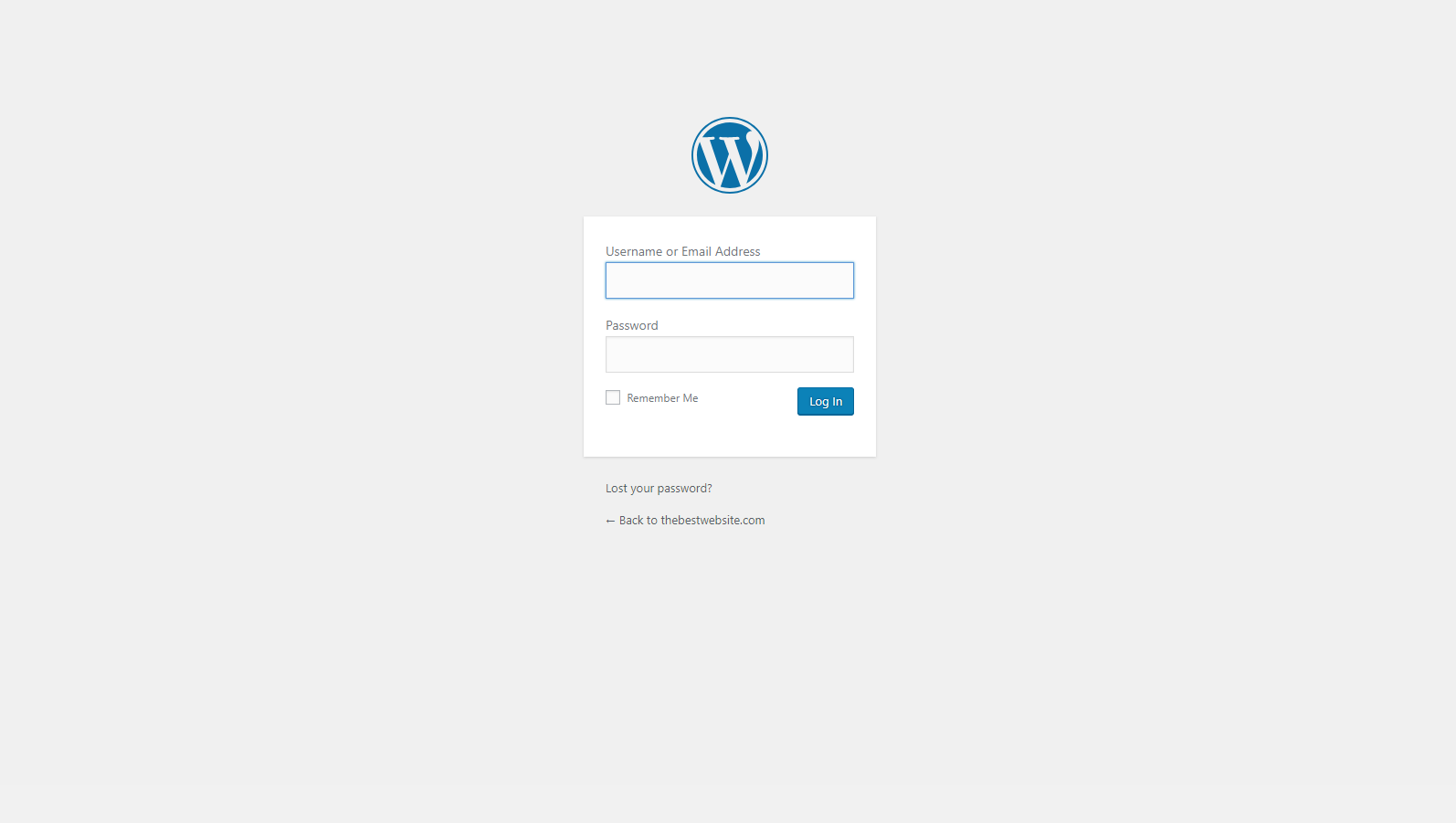
Enter your Username and Password and Log In to be taken to the Administrator Dashboard.
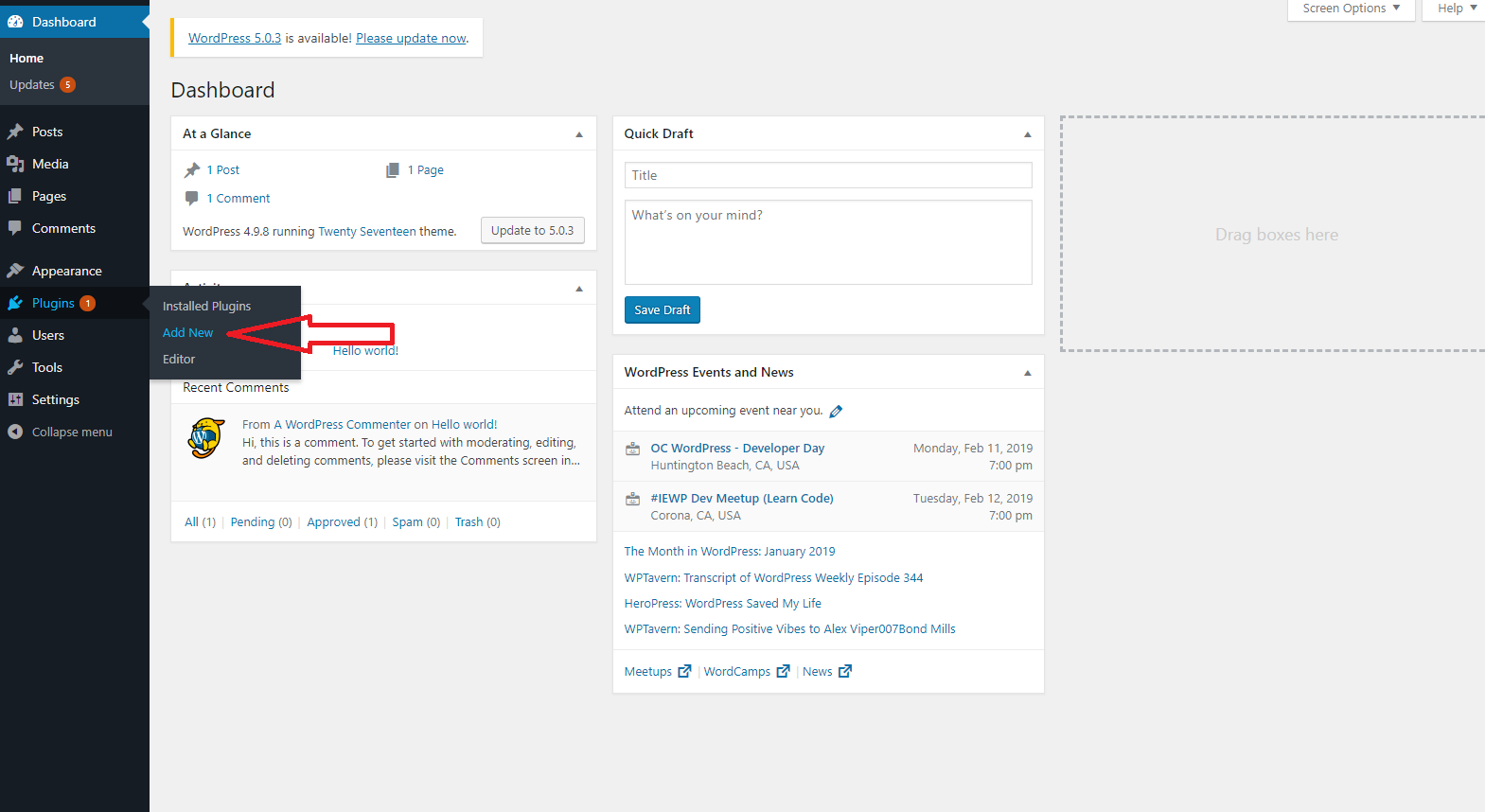
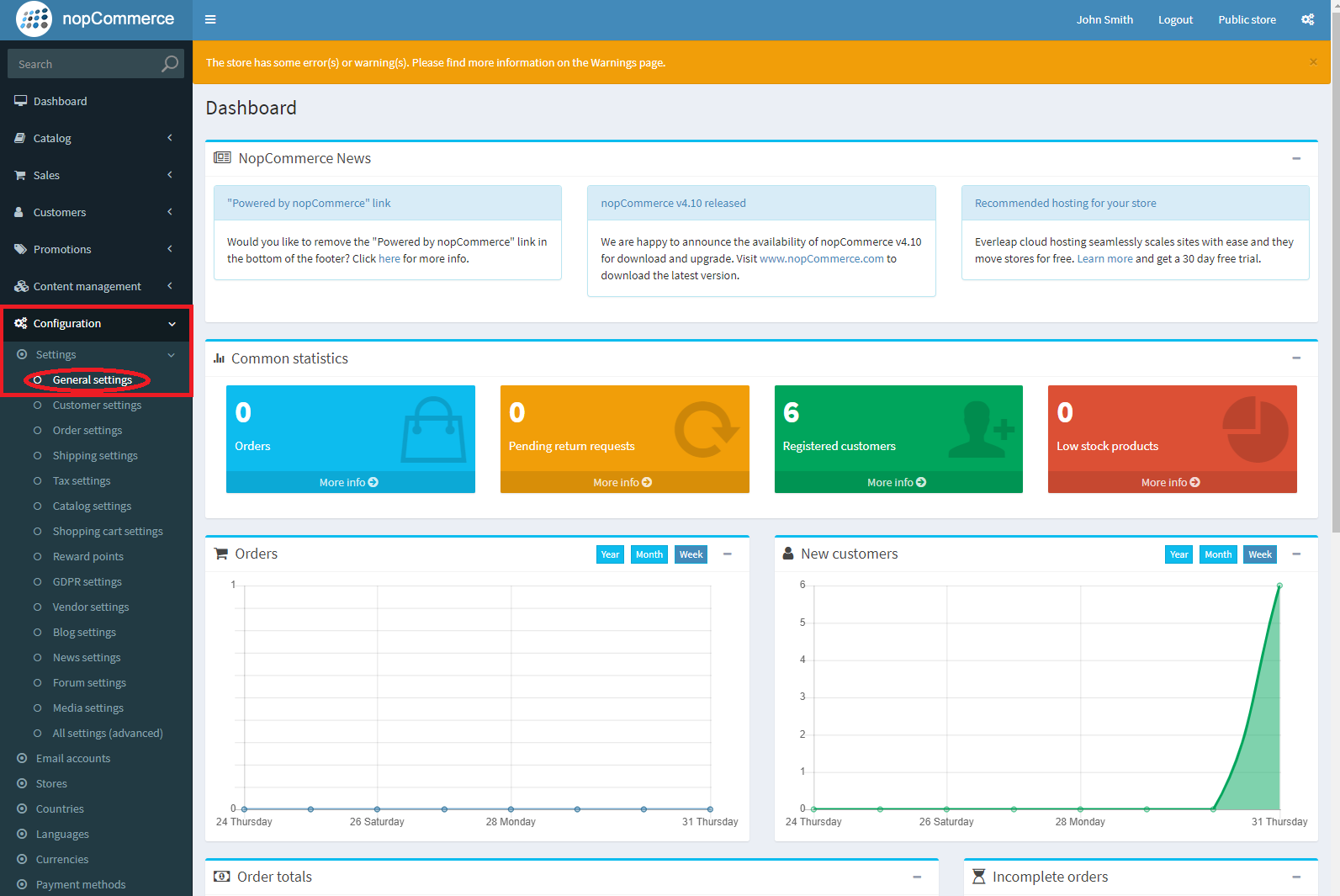
From the Dashboard, head down to Plugins – hover over it for a second and in the sub-menu click on “Add New”.
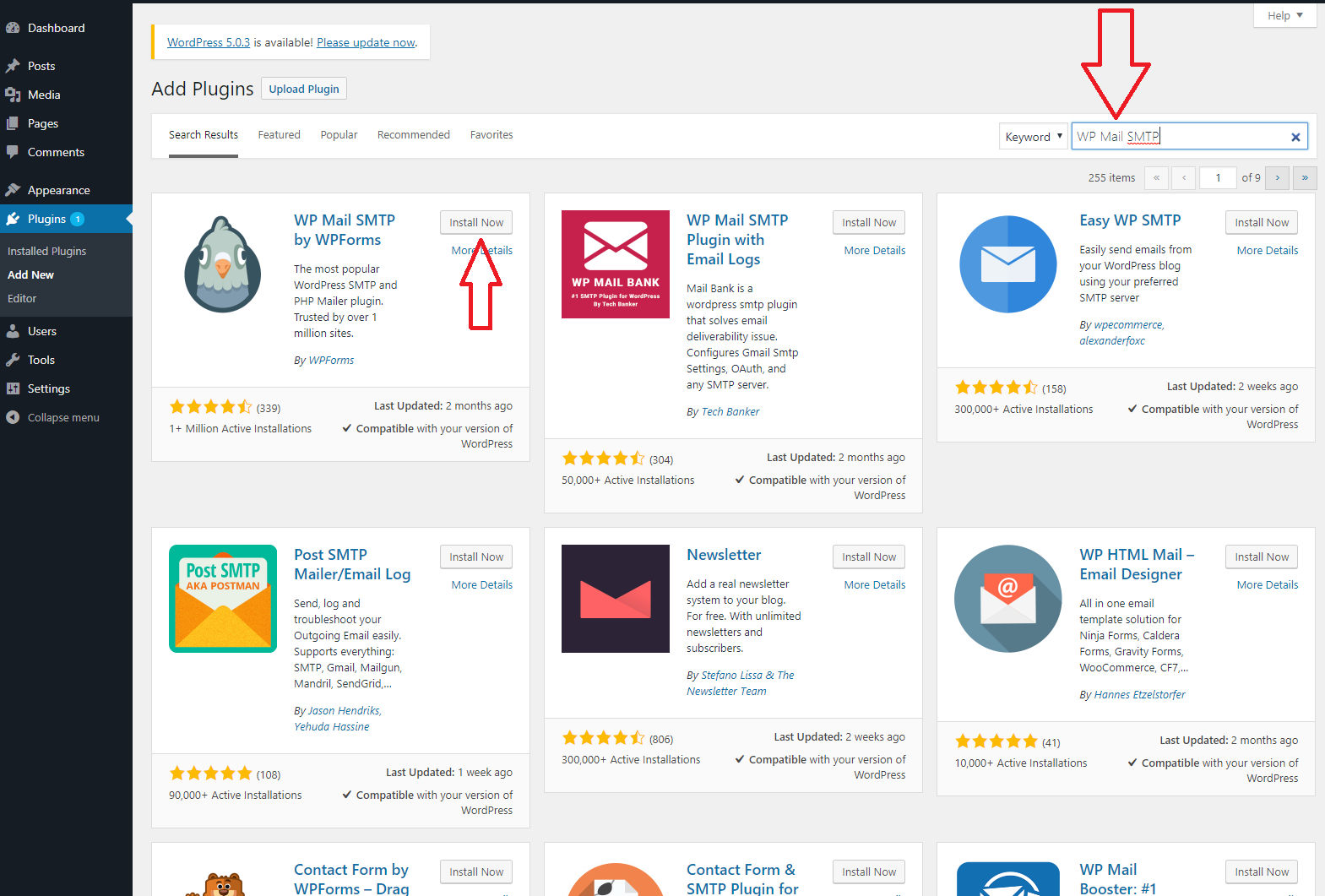
From the Plugins store go to the search bar in the top right and enter “WP Mail SMTP”. The one you’re looking for should be the first option with the bird as the icon. Go ahead and click on “Install Now”. Wait for the plugin to install and click Activate once it has installed.
Now you’re going to want to go to settings and you’ll notice there is now the option for “WP Mail SMTP” Settings.
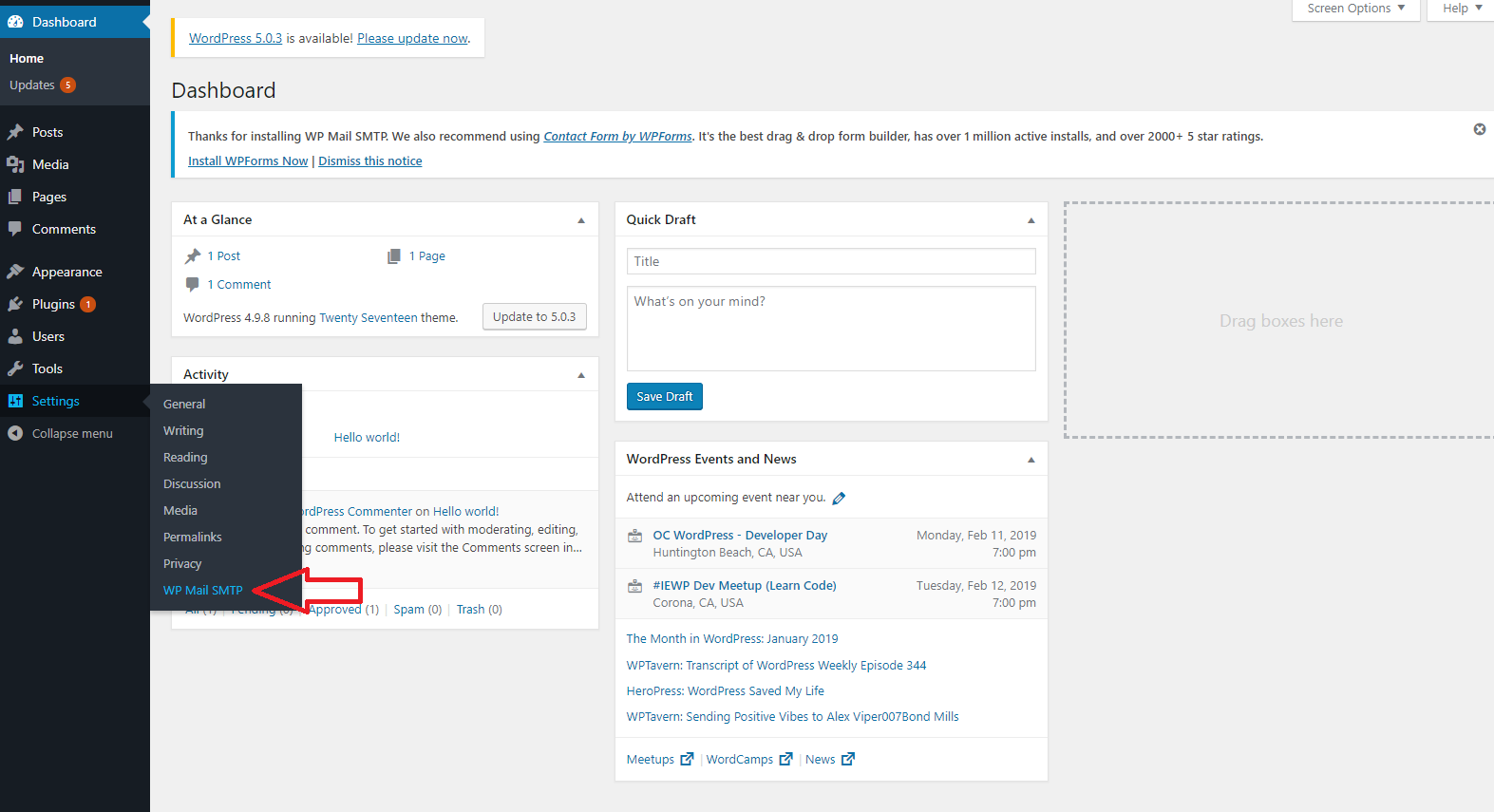
Click on this to be taken to the screen below:
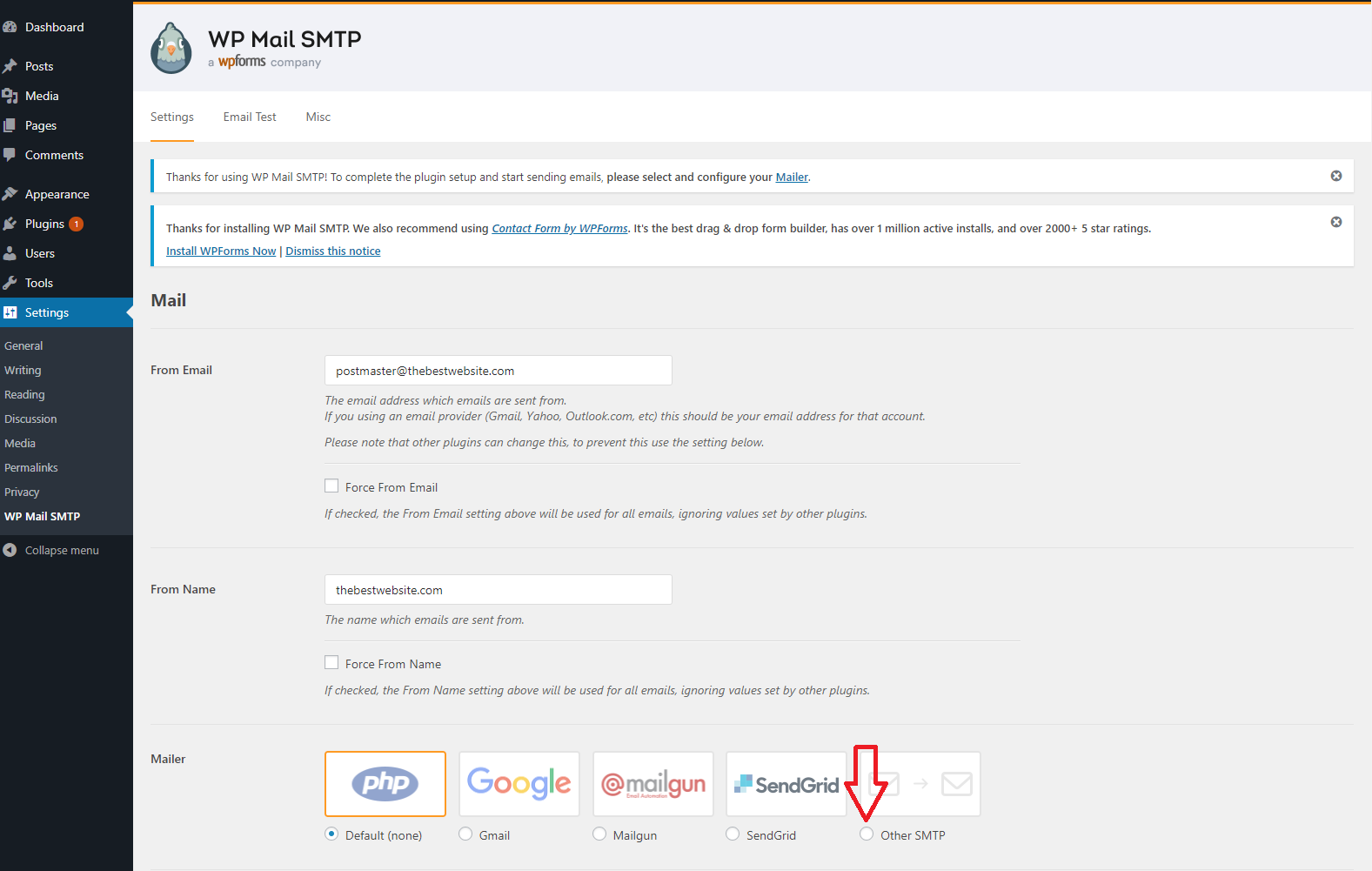
On this page you can adjust some mail settings. The one we want to focus on is in the Mailer section. We want to change this to “Other SMTP” where the red arrow is pointing to above.
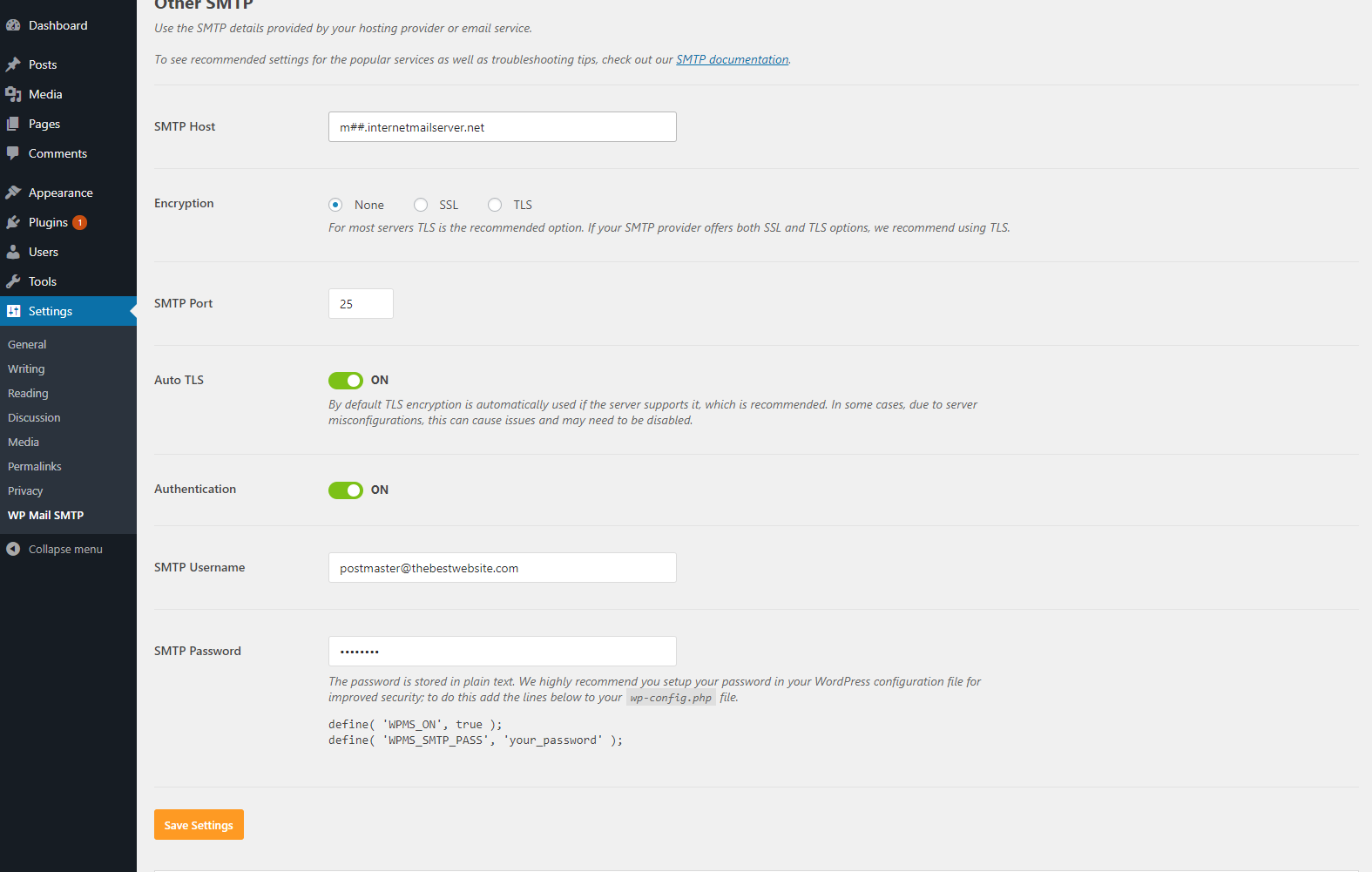
Once you change that, new settings will appear that you must fill out.
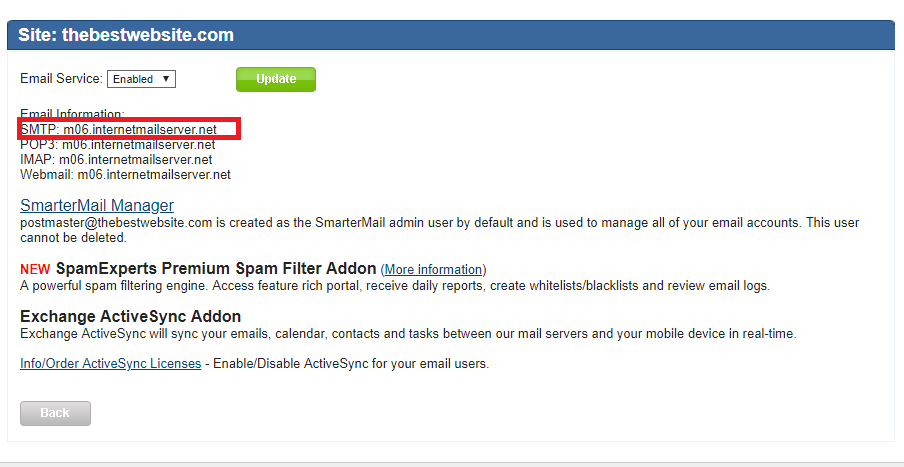
SMTP Host: This can be found in the Winhost Control Panel under Email. You will see your Email server information next to SMTP and should look like m##.internalmailserver.net
Encryption: Leave at None for now
SMTP Port: 25
Auto TLS: Leave this on
Authentication: You’ll want to click this “ON”
SMTP Username: Your full email address
SMTP Password: The password for your email account.
After entering your Email information in all the fields click on Save Settings. This will take you back to the top of the page and everything should be all set (if there was no information entered incorrectly).
You should see a tab for Email Test, go ahead and click the tab and enter an email account you have access to and click Send Email to send a test message. You should be receiving an email that looks like below.
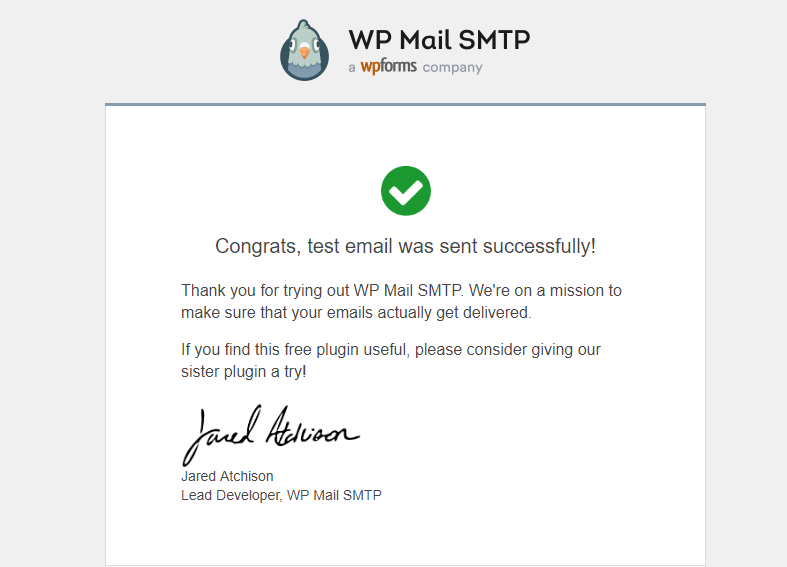
If you received this test email, then congratulations! You are all set to send and receive email through your WordPress site.
If you did not and received an error somewhere along the way, submit a support ticket and we will help walk you through the process.
Visit Winhost to learn more about our WordPress hosting solution
![]()
We have had a couple tickets come in from customers about backing up their MySQL database and how they followed the steps in a previous blog article and ran in to some trouble. I am going to run through the process I used to get this working and hopefully this should clear up any questions and make the process less confusing.
Before we start you will need the to have MySQL Workbench installed. If you don’t have it, you can get it from here:
https://www.mysql.com/products/workbench/
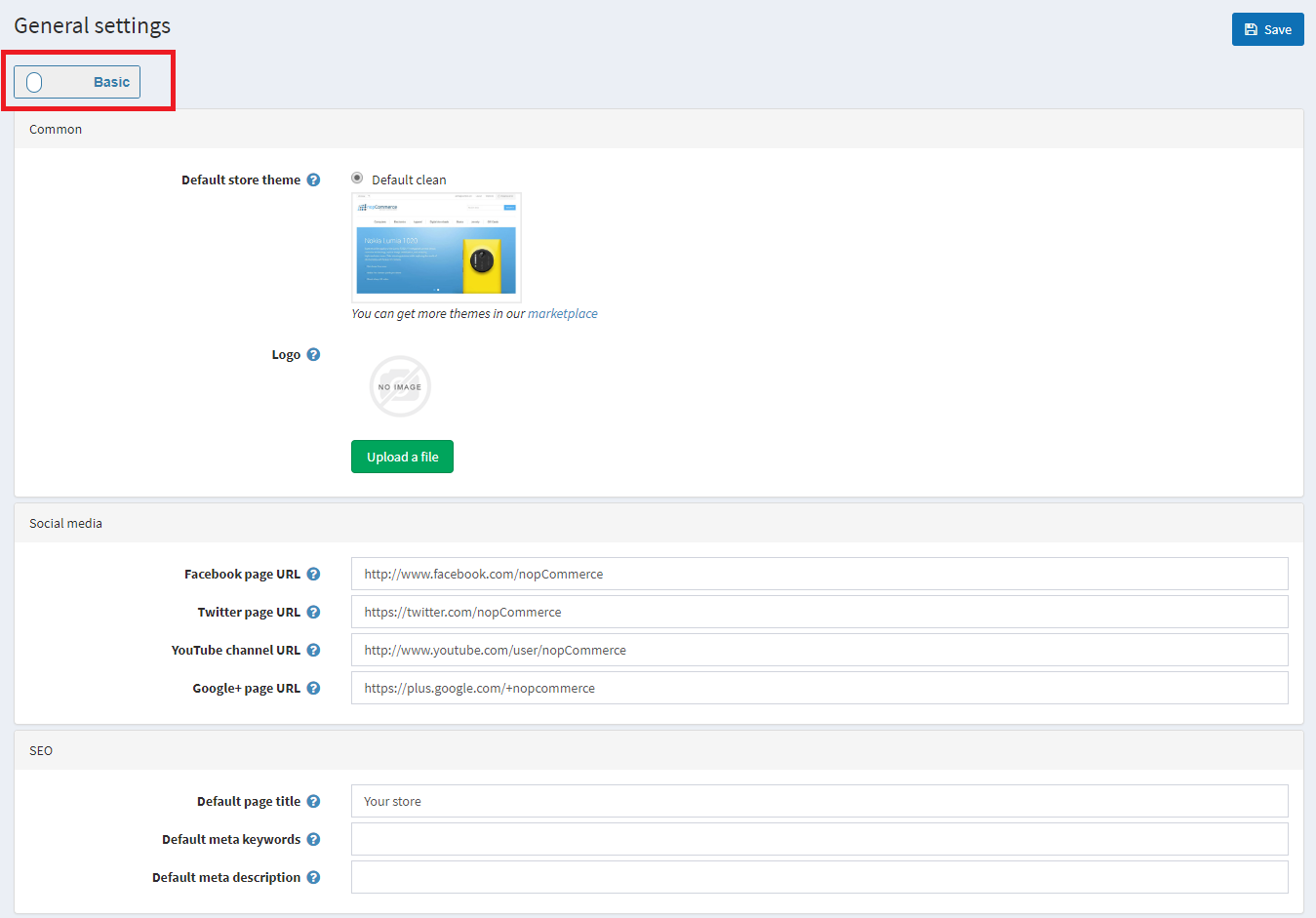
So once you have Workbench installed go ahead and open up MySQL Workbench and you should see the screen below (minus the red arrow). In this post, I used MySQL Workbench v8.x.

You’ll want to click on that plus sign that the red arrow is pointing to (above) and you will be prompted to enter the following info:
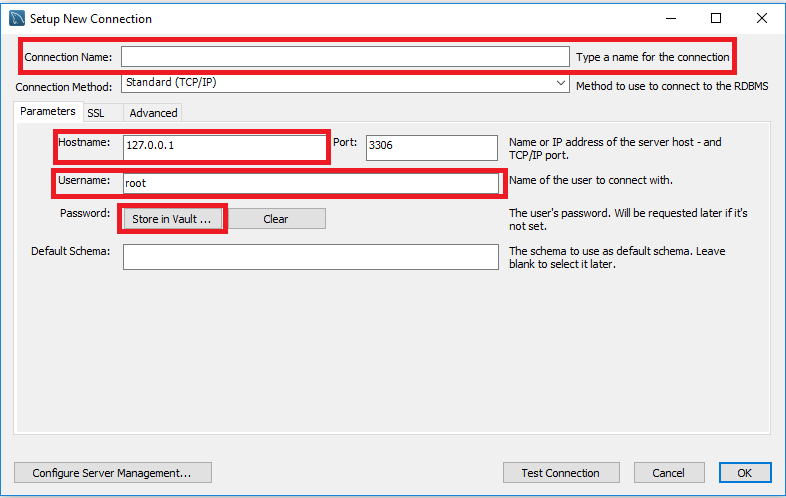
Connection Name: Any name to identify the database.
Hostname: This will be the Database Server found in Control Panel under MySQL | Manage for the database you want to backup. Should look something like: my##.winhost.com
Username: This will be the Database User found in the same place as the last step.
Password: Click on Store in Vault and you’ll be prompted to enter a password. This will be the password set for the database if you never set it, it will be the same as your control panel password.
You can click on Test Connection or OK and it will verify the information you entered and say connection successful. If you get any errors, please double check the information you entered.
After that you should see something like this
Go ahead and double click on your newest connection to connect to the database.
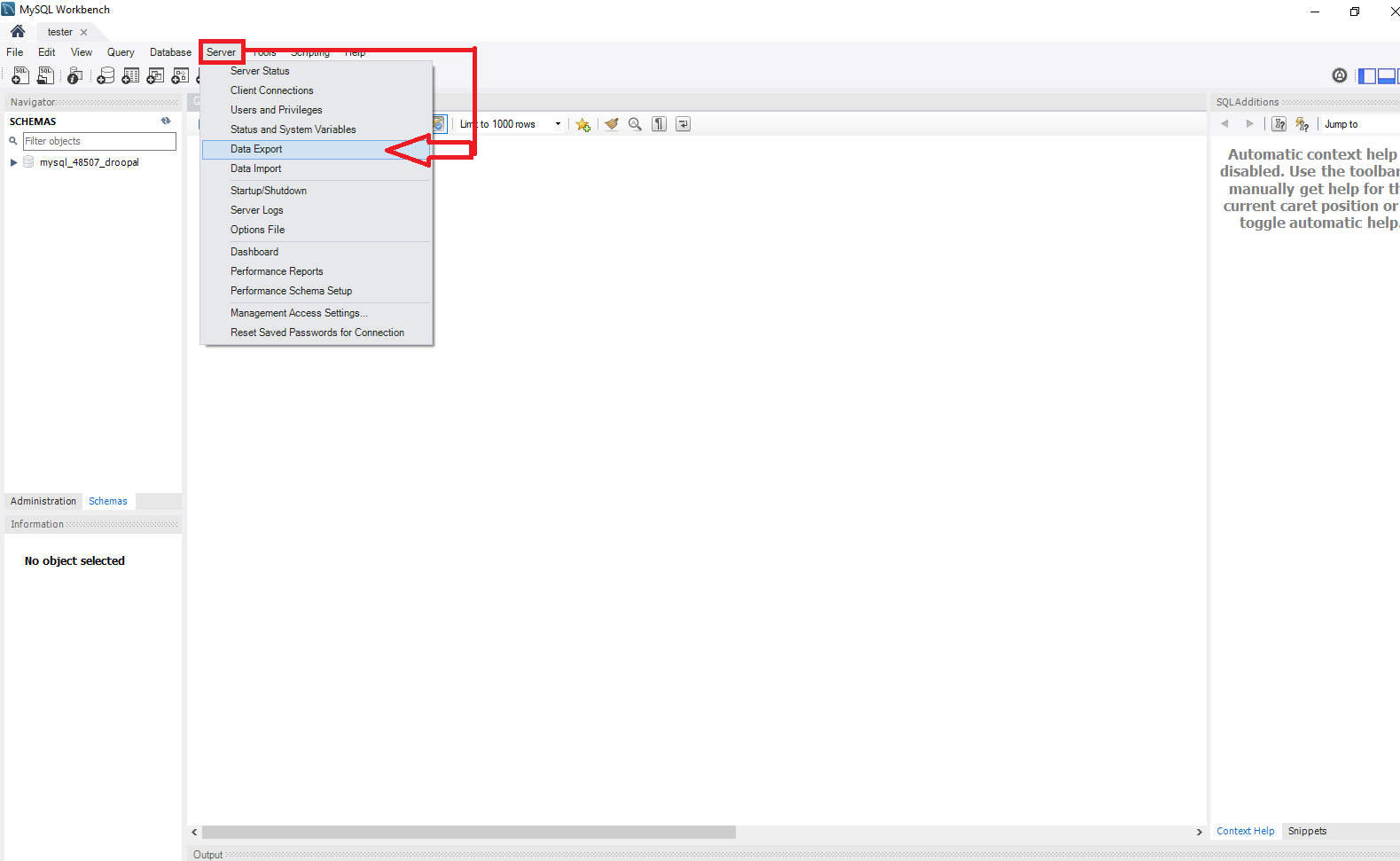
Now to begin the backup process click on Server > Data Export to be taken to a new page.
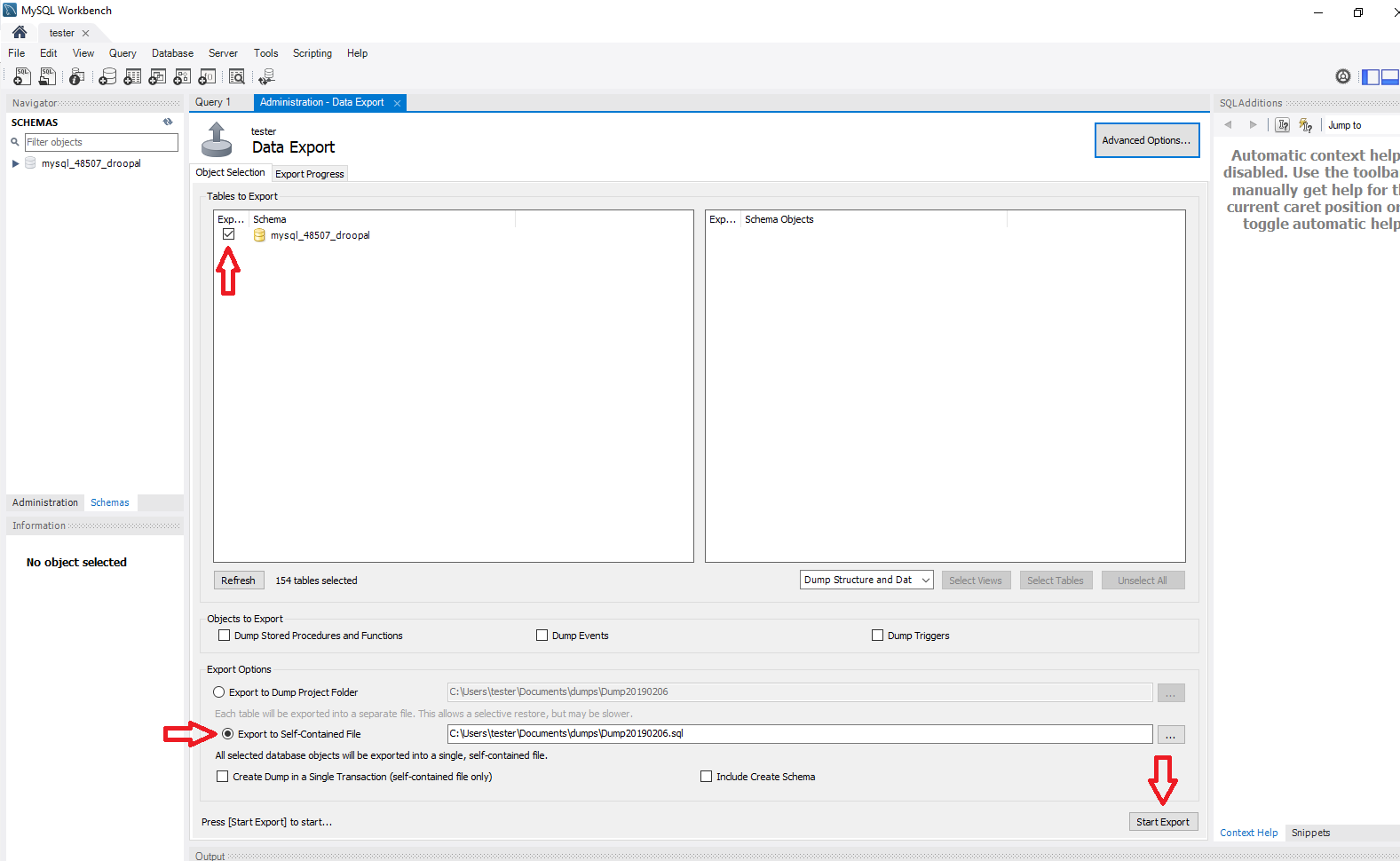
Begin by clicking the checkbox next to the database you want to backup. If you wanted to you can choose specific tables you want to include or exclude by clicking on the database. Make sure you click the option for Export to Self-Contained File and then click Start Export.
If you’re lucky everything works right away and you can find your database dump in the specified file path. If you’re like me however, you might get a warning like this.
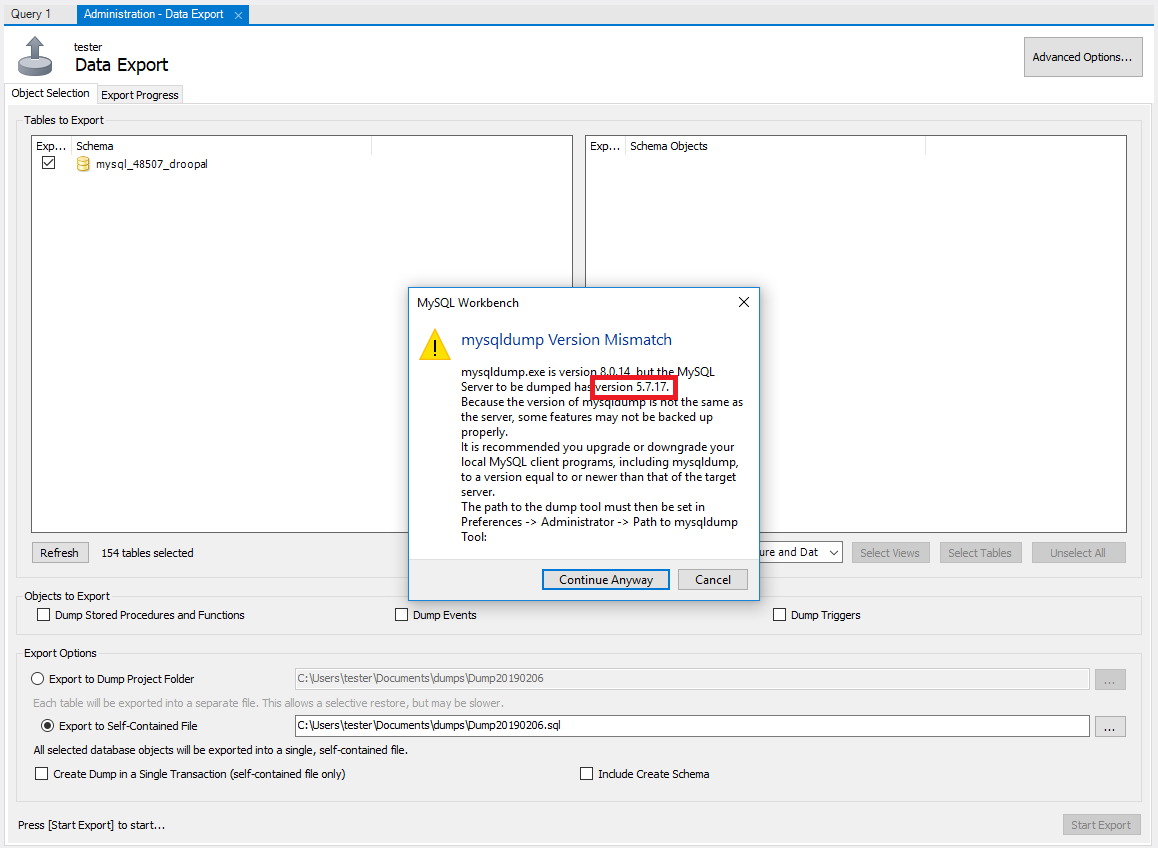
Now you can go ahead and try clicking Continue Anyway, but you will probably end up getting an error code that ultimately ends with “Operation failed with exitcode 2”. So, you’ll want to take a closer look at that warning you received particularly the version number that I have outlined in red. This could be a different number so make sure to check your warning message and not just use mine in this example.
Go to this link: https://dev.mysql.com/downloads/mysql/
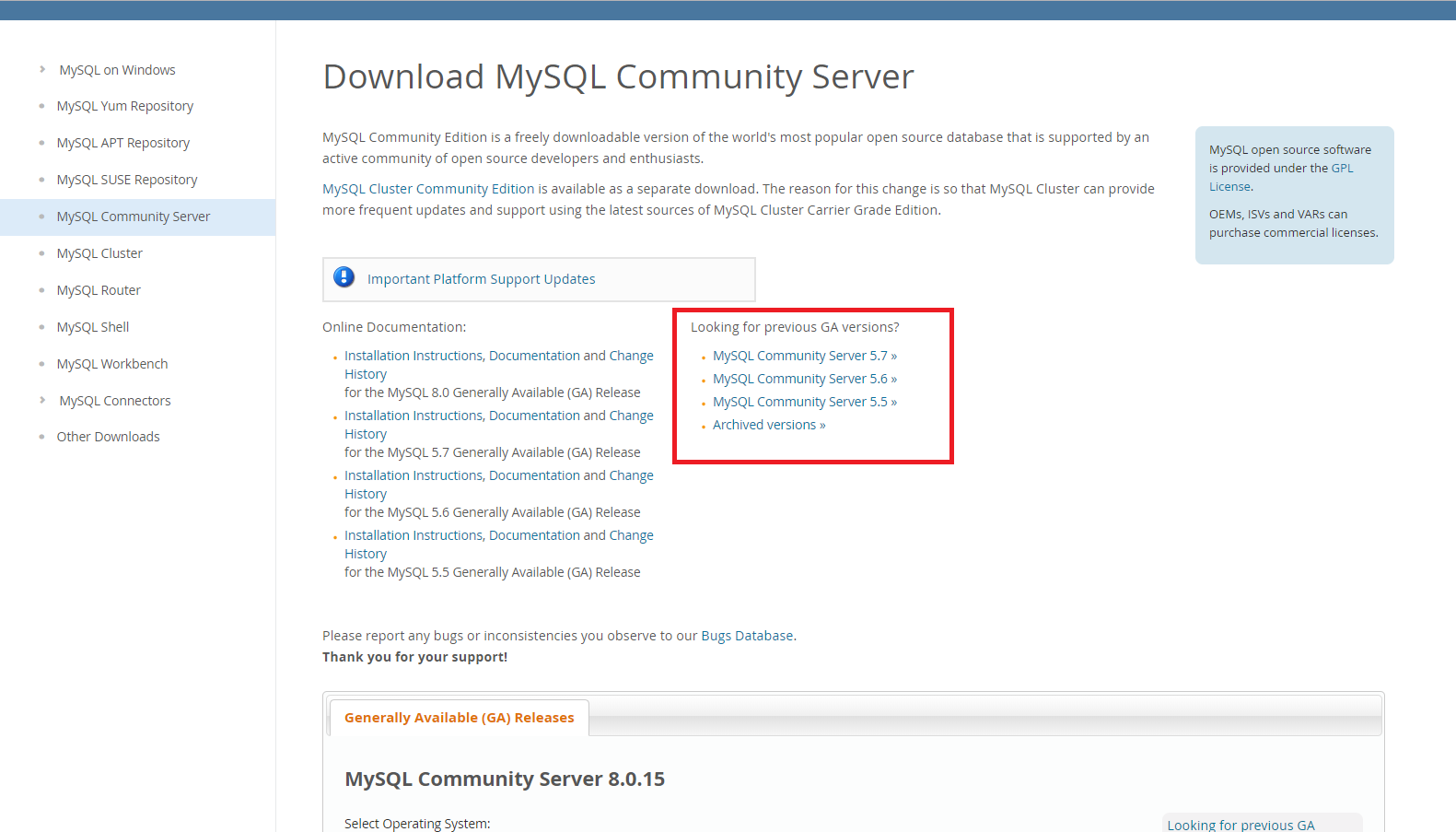
Look at the version that was outlined in red in the previous picture and look for the Community Server with the numbers matching the first two of your version number. In my case I’m looking for Community Server 5.7.
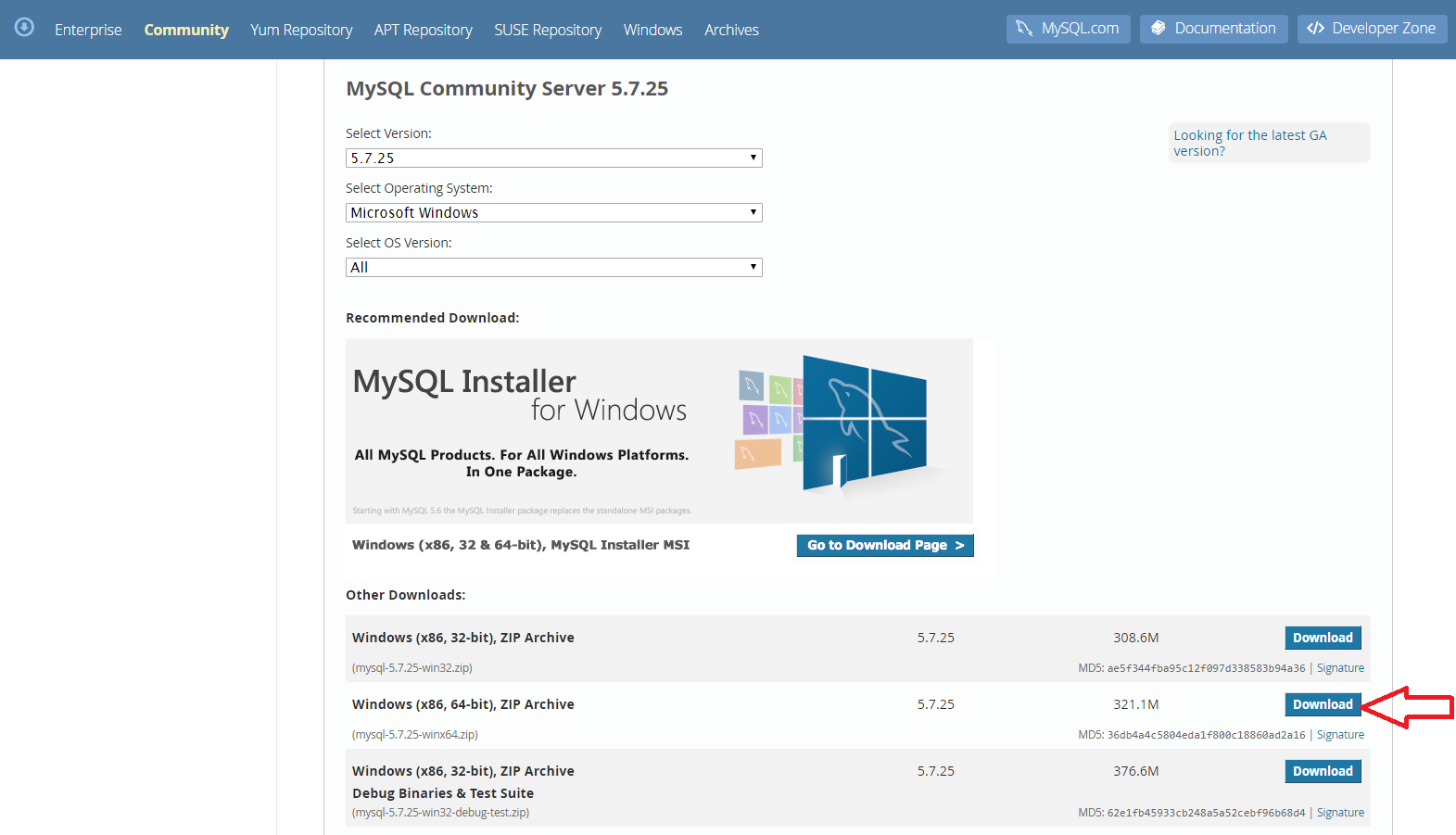
Download the Zip file for your local machines operating system in my case Windows 64-bit.
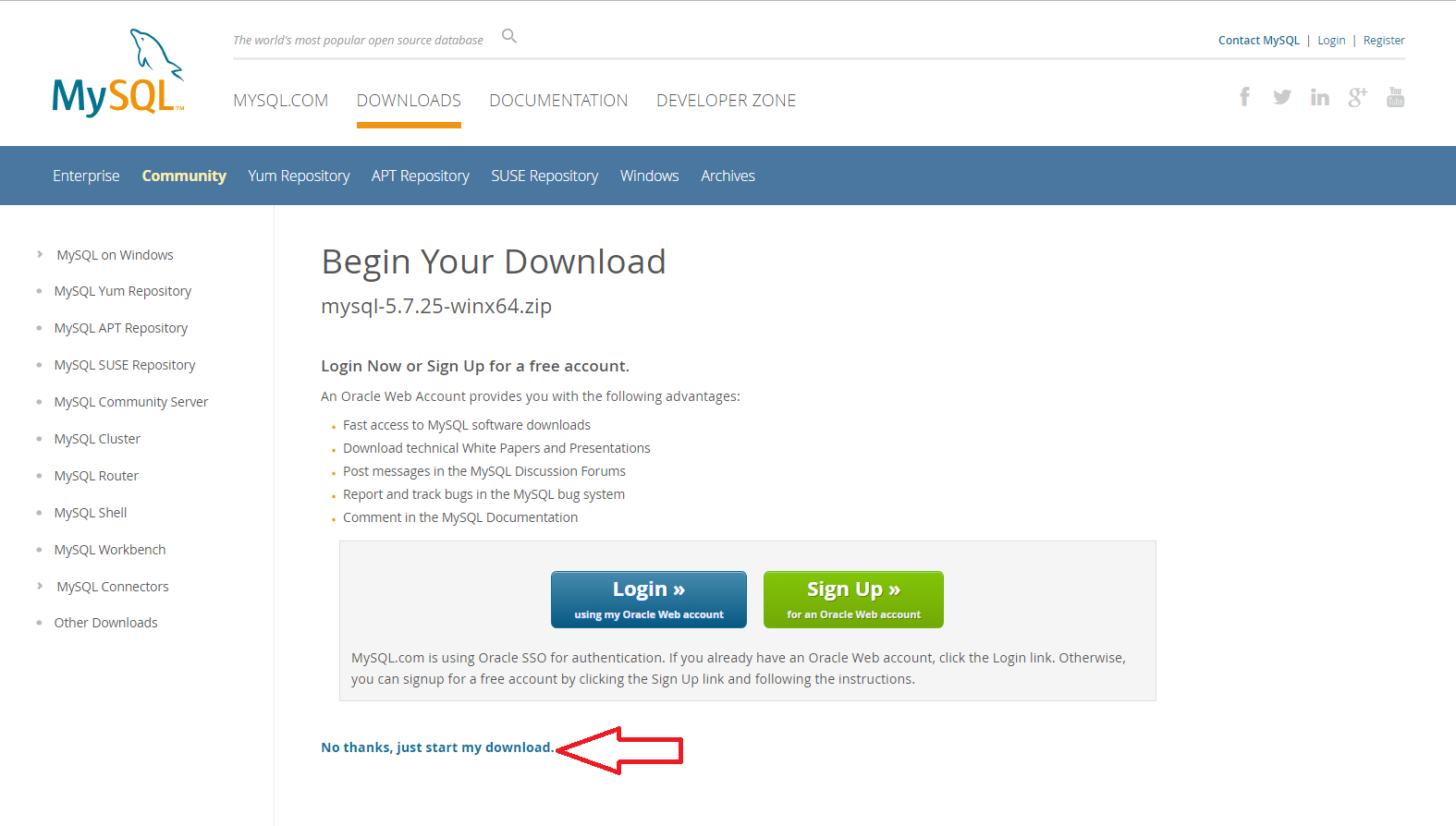
You can create an account or login if you like, I just go to “No thanks, just start my download”. Once it completes open the zip and move the folder onto your desktop.
Now back to Workbench, go to Edit in the top left then click on Preferences and in there you want to go to the Administration tab on the left highlighted in blue.
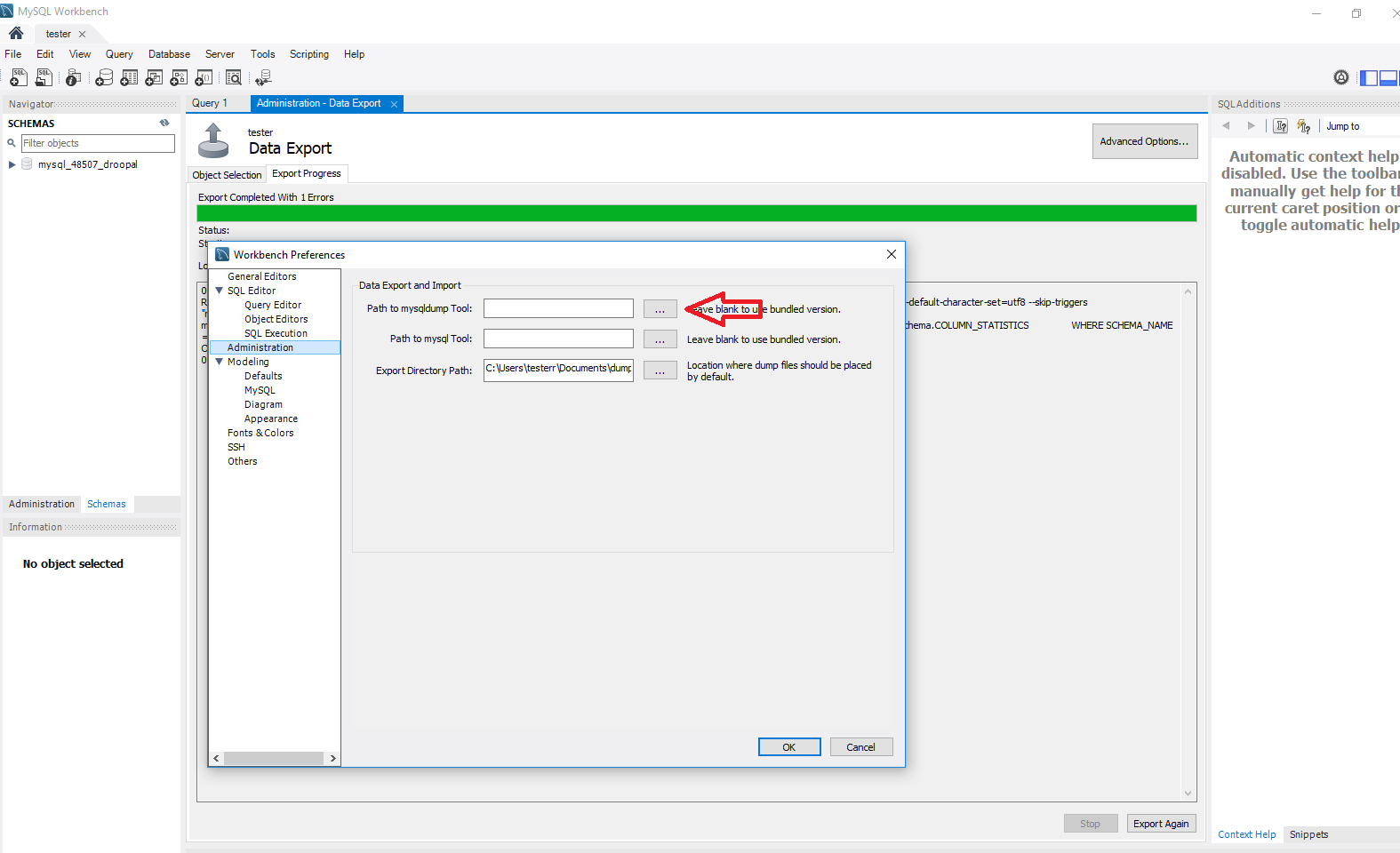
Next to “Path to mysqldump Tool” you want to click on the three dots and locate that folder we just downloaded. If it’s on your Desktop, then the path will be This PC > Desktop > mysql-5.7.25-winx64 > bin. Your version number might vary a bit. Once in “bin” look for the application called “mysqldump” and double click it and then click OK.
Now for the moment of truth, click on export and if everything goes to according to plan you should be seeing something like this.
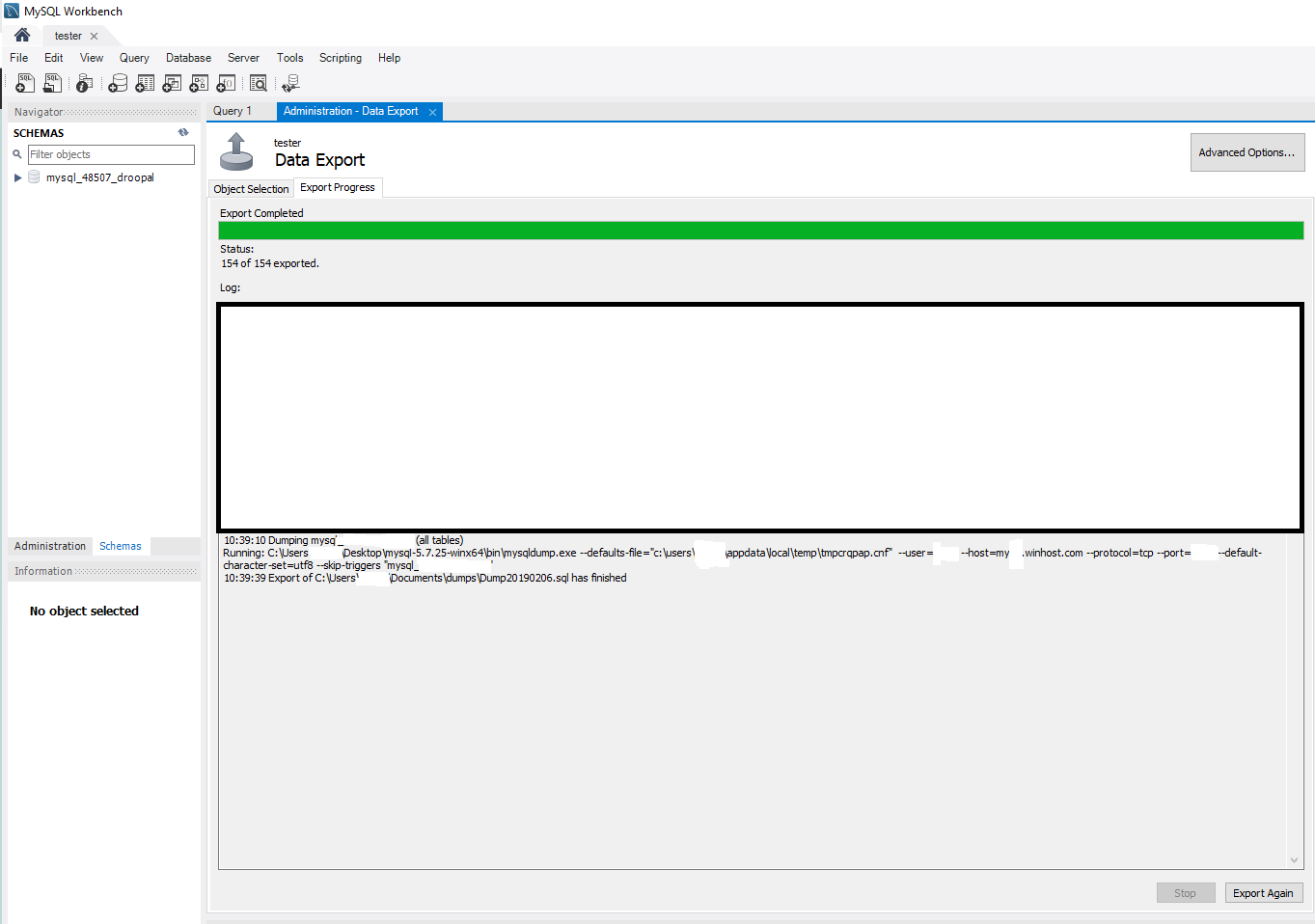
Congratulations! You have successfully backed up your MySQL database.
If you have encounter with this, open a Winhost support ticket.
Visit Winhost to learn more about our mySQL hosting solution
![]()
One of our nopCommerce hosting customers was getting major spam on their site so we suggested to add CAPTCHA and this helped get rid of the spam and their headaches. In this post, I’ll describe the steps to enable CAPTCHA on your nopCommerce store so you can stop or reduce spamming activities on your site.
CAPTCHA is a great way to prevent bots from running wild. The seemingly simple test can prove to be an difficult task for a computer program attempting to spam your site.
In this post, we are using nopCommerce 4.10.
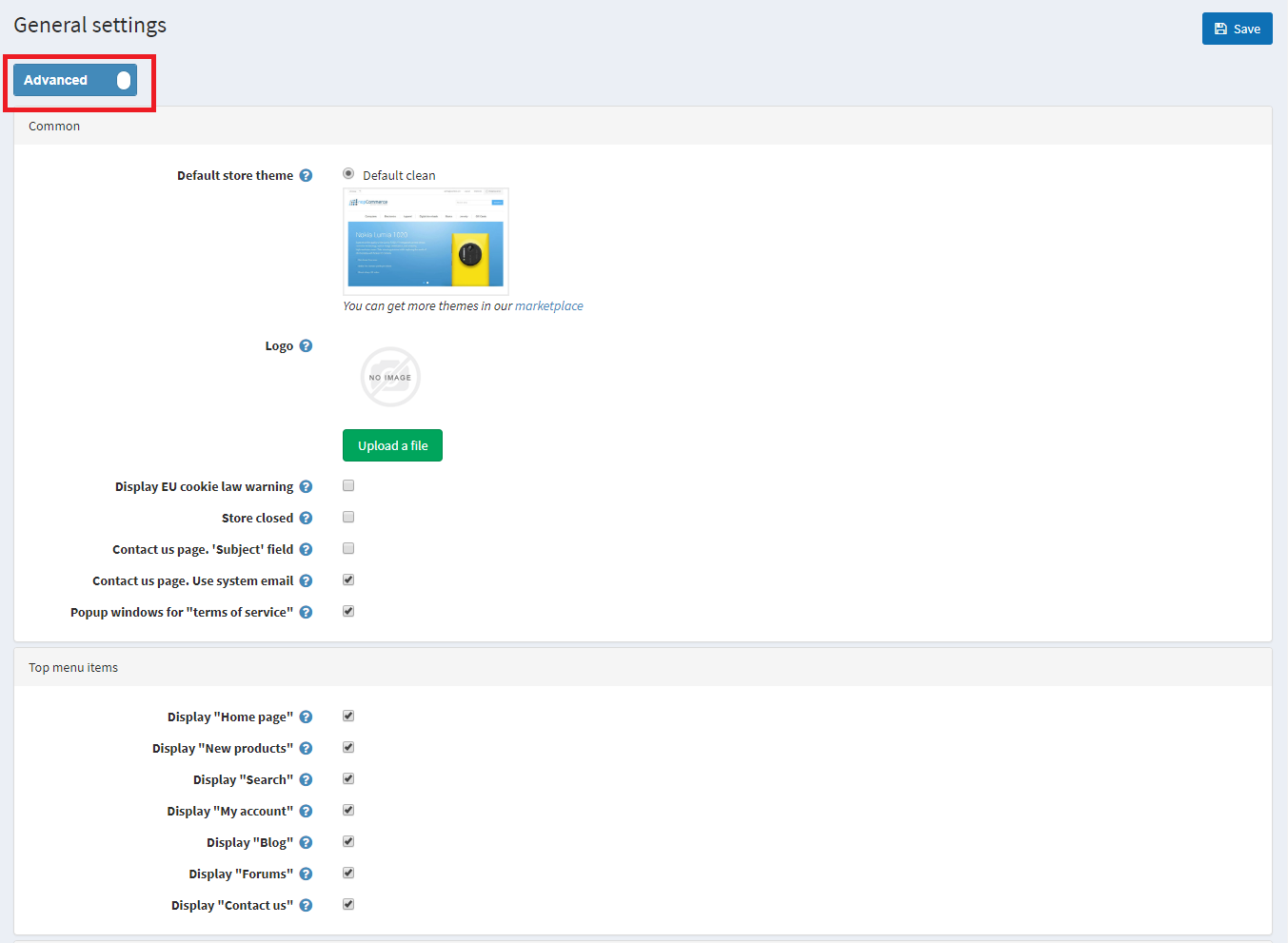
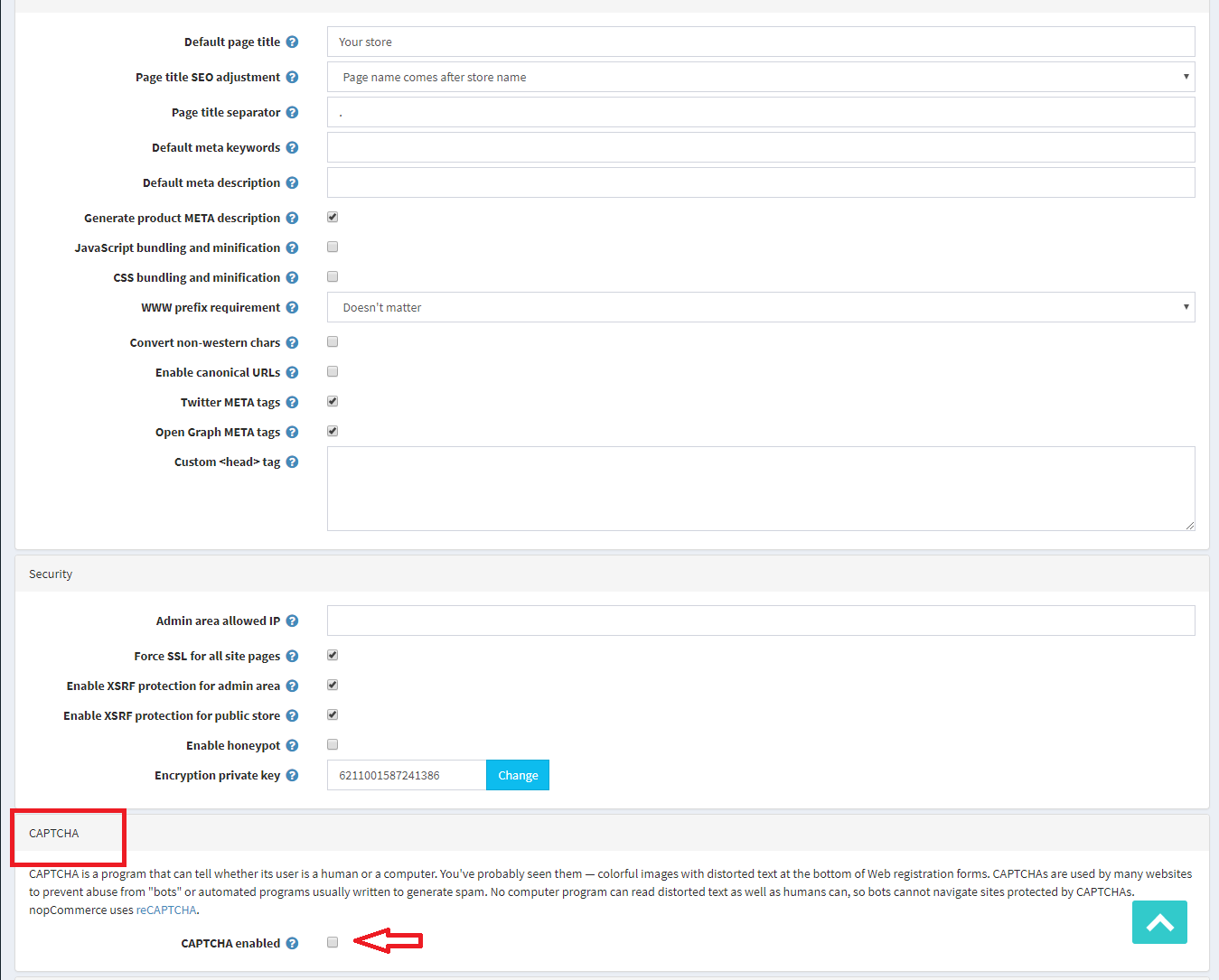
**For testing I recommend NOT enabling “on login page” just yet.
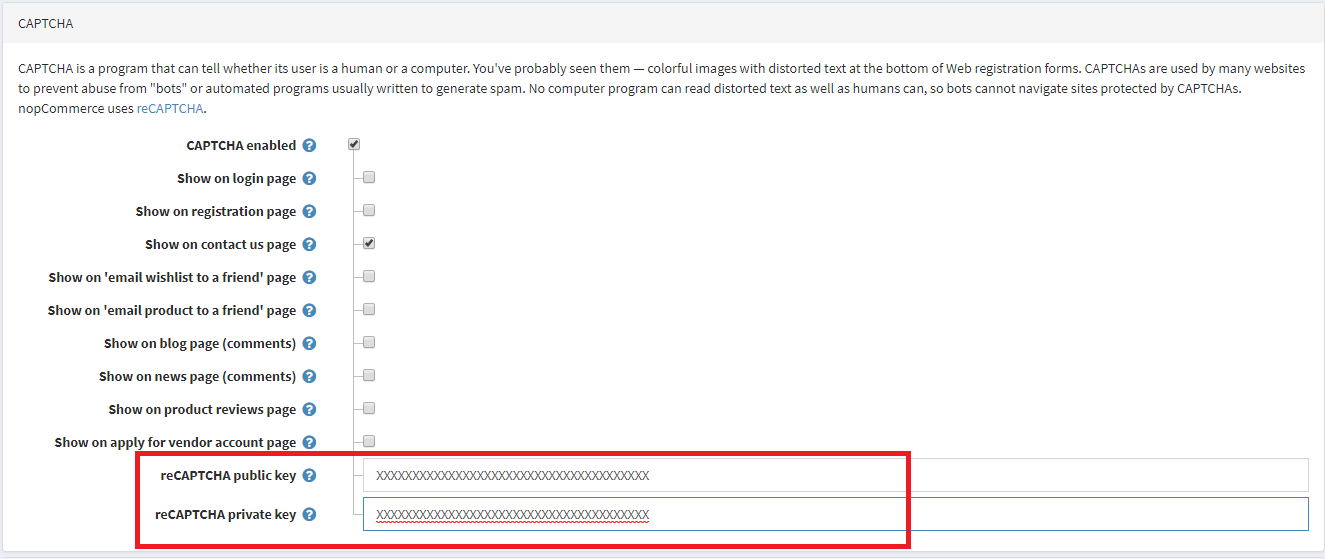
***Note: Be sure to test it before checking the “Show on login page” – if done improperly you can end up getting locked out of your account.
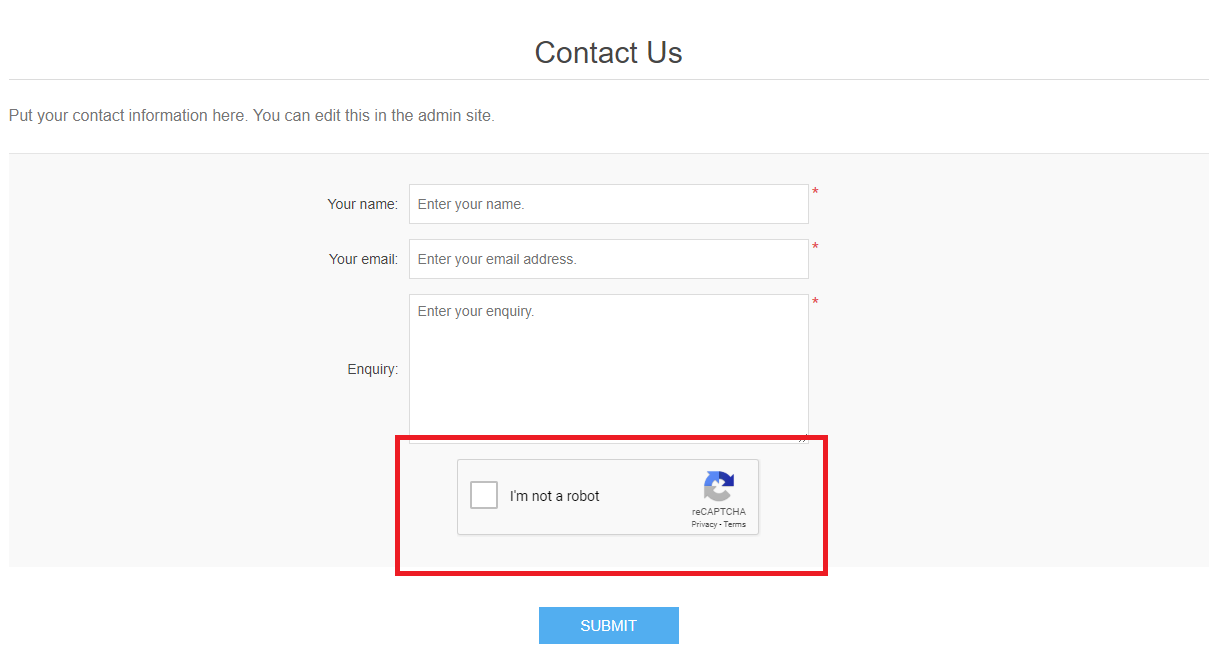
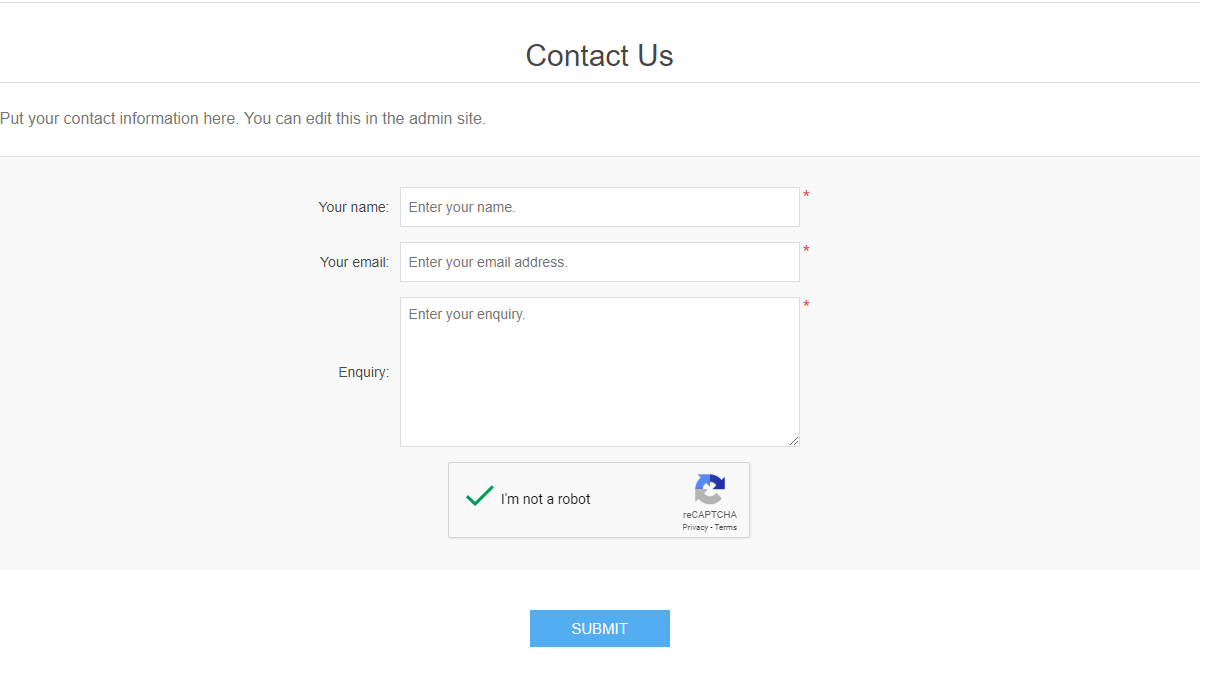
I hope that this helps you prevent getting bombarded by spam.
Visit Winhost to learn more about our nopCommerce hosting solution
![]()
Years ago, I wrote an article on how to configure Elmah to be used on Winhost. You may have noticed that there is no official support for ASP.NET Core, however, you can use ElmahCore by barestan to perform the same logging to a database, and this blog provides an example on how to set that up.
First, we’ll start by creating a New Project in Visual Studio:
services.AddElmah<SqlErrorLog>(options =>
{
options.ConnectionString = @"connection_string";
});
app.UseElmah();
That’s it. If you want to know if it’s working, you can generate a sample exception like this:
app.Run(async (context) =>
{
await context.Response.WriteAsync("Hello World!");
int[] numbers = new int[5];
await context.Response.WriteAsync(numbers[6].ToString());
});
That will generate an “Index was outside the bounds of the array.” exception which will be logged into the database. You can query the dbo.ELMAH_Error table to see the results.
Visit Winhost to learn more about our .NET Core hosting solutions
![]()
This little factoid should freak you out: More than 80,000 websites are hacked every day.
That’s almost one every second, or about 29 million every year. Those numbers translate to a lot of pain and inconvenience for a lot of people. Count yourself lucky if you’ve never been one of them.
There are a quarter of a billion domains with active websites. If 29 million sites are hacked every year, that means we’re living in a world where more than 1 in 10 websites are likely to be compromised. Every year.
How does this happen?
Security starts at home. It’s an old saying, but it applies to a lot of website compromises. We see a lot of hacks that aren’t actually website hacks at all, because the perpetrator is using valid FTP login credentials that were harvested by logging keystrokes or reading log files on a home computer or laptop that has been infected with a virus or malware.
But perhaps the most common way in to a website or server is through old, unpatched third-party software. And a large percentage of that old, unpatched third-party software is WordPress, or WordPress plugins.
Before I give you some tips on locking up your WordPress site, I’d be remiss if I didn’t mention that Winhost has a fully managed WordPress hosting, security and hardening service. The service includes WordPress hardening for maximum security, WordPress-specific support and personalized assistance, and maybe most importantly, monthly updates of WordPress core, Plugins and Themes. The monthly updates consist of one of our in-house WordPress security experts personally examining your WordPress installation for malicious files and signs of compromise. If we discover that your WordPress installation is compromised or hacked, we’ll clean up the mess.
Okay, that’s it for the sales pitch. But if you’ve ever had to clean up a WordPress compromise, I’m pretty sure that you’ll be able to see the value in that service.
The first step in WordPress security doesn’t have anything to do with WordPress itself, but rather site backups. If you always have a current backup, it’s much easier to bounce back from a compromise. Simply identify your most recent “clean” backup, delete everything on your site and upload the clean backup.
We do periodic backups of our entire network for disaster recovery purposes, so if you are compromised you could just request a backup from us. The problem with that approach is we back up every day, and we only retain one copy of those backups. So if you don’t notice that your site has been compromised for a few days, our backup will likely be a copy of the compromised site. That’s not going to be of much help.
So we recommend a cloud backup service. There are a lot of them out there, or you can set one up from your Winhost Control Panel with a few clicks. Our SiteBackup service backs up your website files and databases on a schedule that you choose, retaining as many versions of the backup as you want to keep.
Okay, so that’s a good place to start, with a daily backup of your WordPress site and database. Next are a number of things that you should do to prevent a compromise of your WordPress site.
Update, update, update
How often do you log in to the admin section of your WordPress site? If it’s less than every week – or even every month – you need to start checking in more regularly and updating both the core WordPress files and all of your plugins. If you use a plugin and can’t remember ever updating it, check out the plugin’s page on WordPress.org and make sure it hasn’t been abandoned. If it seems like it has, uninstall it. Chances are there’s a well-maintained plugin out there that will do the same thing.
Kill the admin user
If you installed WordPress some time ago, it may have created a user named “admin” by default. Most brute-force WordPress hacks attempts are on the “admin” username, so you don’t want it to be there. To check, go to your Users page (/wp-admin/users.php) and see if admin is listed there. If it is, create another user or give another existing user the administrator role and delete the default admin user.
Don’t use the default WordPress MySQL table prefix
If the bad guys do manage to find a vulnerability within your site and one of their attempts is to query a table or insert into a table and you used the default table prefix, you could be in trouble. When you’re installing WordPress it’s best to change the table prefix from the default “wp_” to something different. One easy way to do that is to insert random characters after “wp_” – for example wp1od02l_ or wp5434fs_.
Change the WordPress login error
By default, WordPress gives hints about your login when a login fails. One of the steps in our hardening service is to change the login error to “You have entered the wrong Username or Password!” That way someone trying to compromise your site will never know if the username or password is incorrect, making it much more difficult to force or guess a login.
Remove the WordPress version information
It really helps the bad guys to know which WordPress version you’re using. Once they know the version, they can try known vulnerabilities giving them a better chance of getting into your site. They’ll also use Google to find WordPress blogs running a specific version of WordPress that’s easily hackable. You can use a plugin to remove version information.
Disabling Theme and Plugin Editing
The theme editor within WordPress is there to allow you to make quick changes to the code within a theme’s files. Chances are you won’t ever use that feature, but you can be pretty sure that the bad guys will make use of it to enter malicious code. In fact, that is how a lot of WordPress sites get hacked. To prevent that, enter the following rule in your Wp-config.php file, right before the “Stop Editing” tag:
/** Disable File Theme and Plugin Editing */ define('DISALLOW_FILE_EDIT', true);What else?
The Winhost hosting environment goes the extra mile by disabling executable files from running within the uploads folder, as well as IP restriction of the wp-admin directory. That way the wp-admin directory can only be accessed from IP addresses you specify.Last but not least, install a Security plugin
If you haven’t already done so, we would highly recommend installing one of the WordPress security plugins. As part of our hardening service we make the security plugin a “Must Use” plugin. That means the plugin can’t be disabled from the admin section of WordPress. The only way to disable it is by deleting the plugin via FTP.That’s a lot to install, configure and keep track of, but following these recommendations will make your WordPress installation much less susceptible to compromise. If it all sounds good but you don’t really have the time or inclination to do it yourself, let us do it for you.
The great thing about ASP.NET Core is that it’s portable, allowing you to run your Core application on any OWIN-compatible server. So, even if a particular version of .NET Core is not installed on the server, you can still deploy your Core app in “self-contained” mode.
In this example, we’re going to use the Orchard Core application. Orchard Core is a re-write of the original Orchard application (the thing that runs all the MSDN blogs) in ASP.NET Core. As of the time of this writing, Orchard Core is using ASP.NET Core 2.0. And, at the time of this writing, we have not yet updated our servers with the newest .NET Core to support ASP.NET Core 2.0 natively, but, to repeat: you can still deploy your Core app in “self-contained” mode.
First, some house-keeping. Make sure you have the .NET Core 2.0 SDK installed and Visual Studio is updated.
Orchard Core supports different databases, SQL, SQLite, MySQL and Postgres. I’m going to use SQL, which is included with all Winhost plans. This is a good time to create the SQL database in your Winhost control panel.
Onto the instructions:
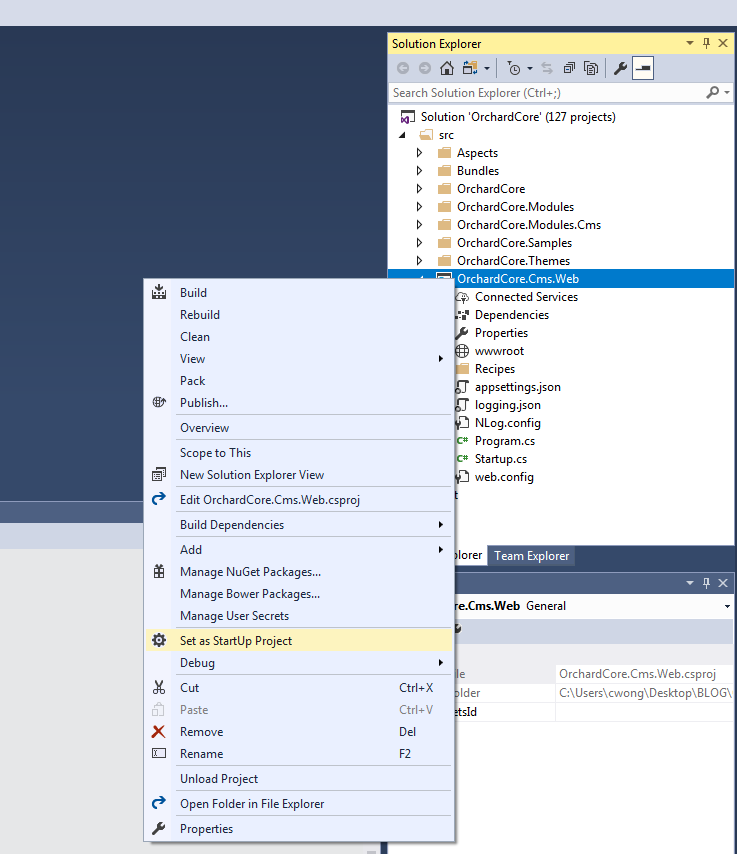
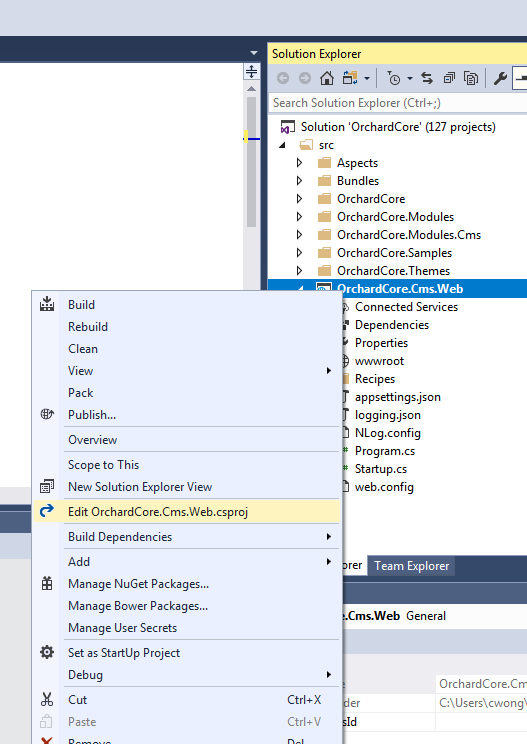
By default, Orchard Core is Framework-dependent. We have to change that to make it self-contained. We have to specify the target platform (tell the application what kind of server it’s going to be running on). In my case, my Winhost site is running on Windows 2012/IIS 8. You can find this information in your Winhost control panel, under the Site Info section. The Runtime Identifier for Windows 2012/IIS 8 is: win8-x64. If you’re site is running on a different server, you can check out the full catalog of Runtime Identifiers here.
<RuntimeIdentifier>win8-x64</RuntimeIdentifier>
Now we’re just about ready to publish. This would be a good time to remove the parts of Orchard Core that you’re not going to use. (For this example site, I didn’t remove anything.)
Before, pre-2.0, we would have run the dotnet restore and dotnet build commands at this point. But now, those are implicit commands with publish. So you can just run the publish command (right-click OrchardCore.Cms.Web and select “Publish…”). I used FTP to publish the project directly onto the Winhost servers. Instructions for different deployment methods are available here.
Wait for the project to publish, then navigate to your site and you should see the Orchard Core setup page:
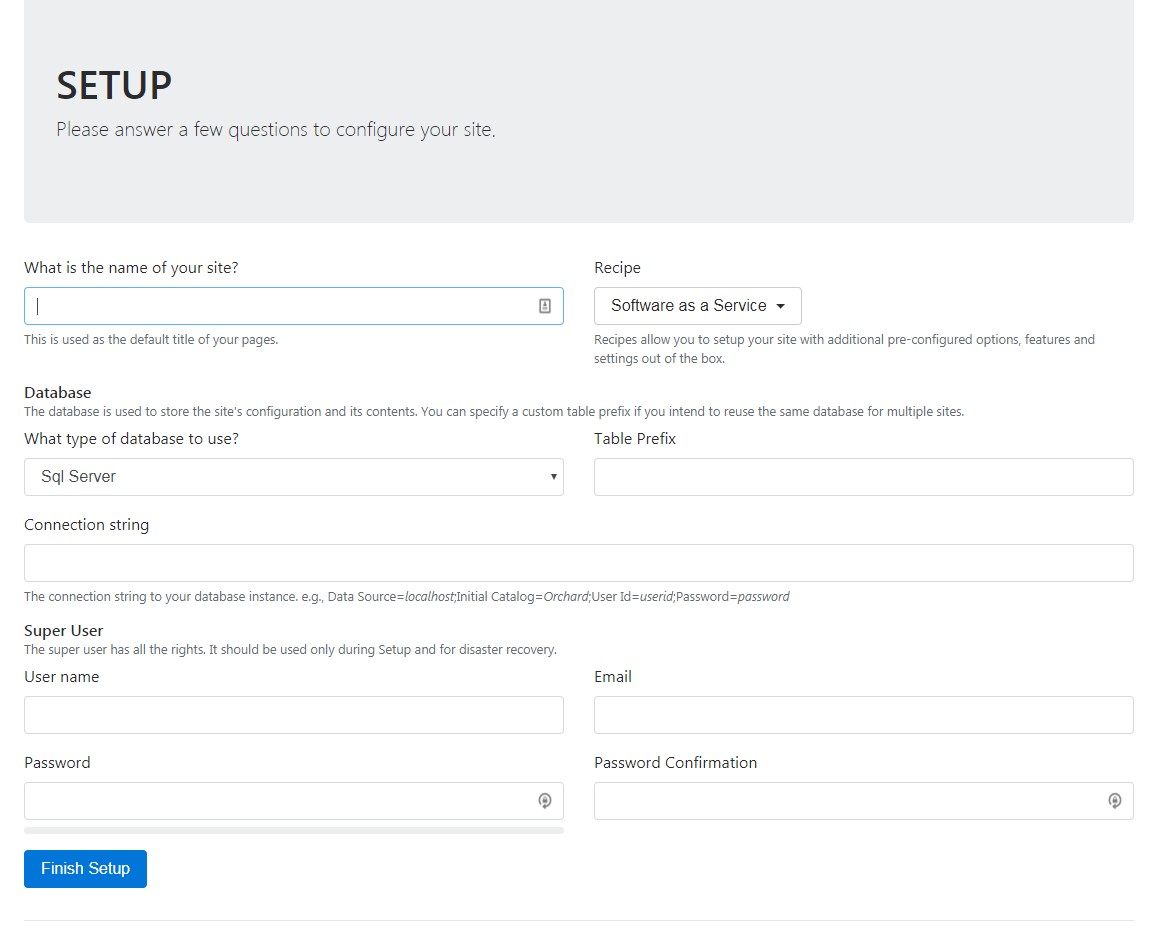
I picked the Agency Recipe. Fill out all the fields, click the Finish Setup button and you should see your new site:
![]()
SpamExperts is a great anti-spam service. It’s easy to use, and relatively inexpensive because you just need one service to cover your entire domain. (Most other spam services require you to buy one service for each of your email addresses.) Our SmarterMail email service (included with all of our plans) comes with some spam-fighting features that allow you to set your own weights and filters. But a lot of our customers were not comfortable with tweaking those weights and filters on their own and risk losing important emails.
SpamExperts is highly effective out-of-the-box. Simply set-it-and-forget-it. In fact, we found it so effective that we switched over to using it for our own corporate emails.
This articles explains how to set up your SpamExperts service.
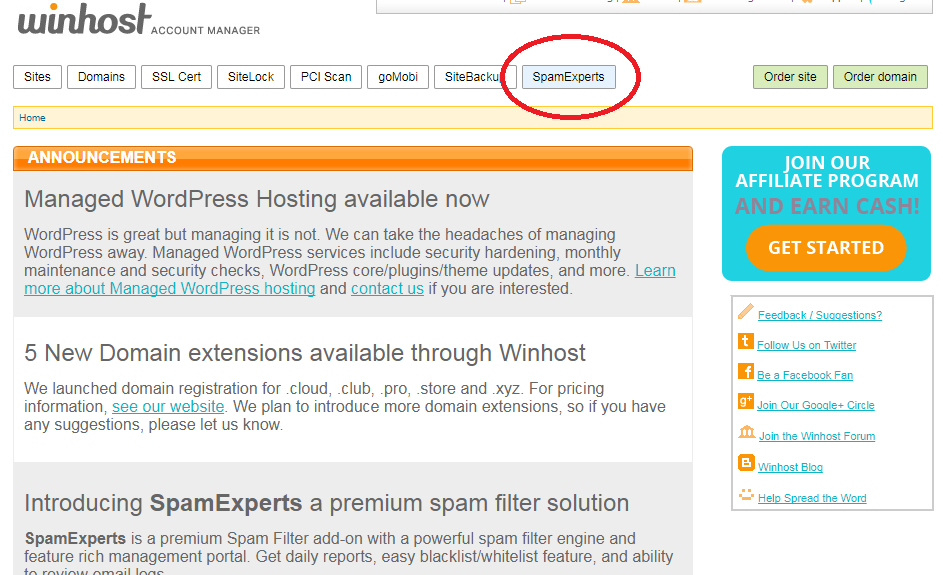
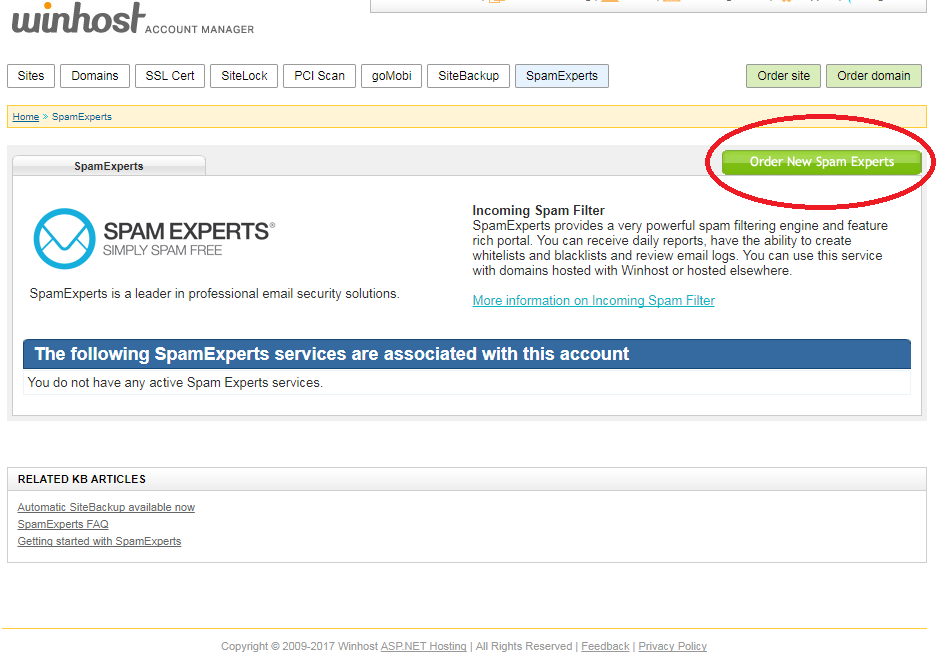
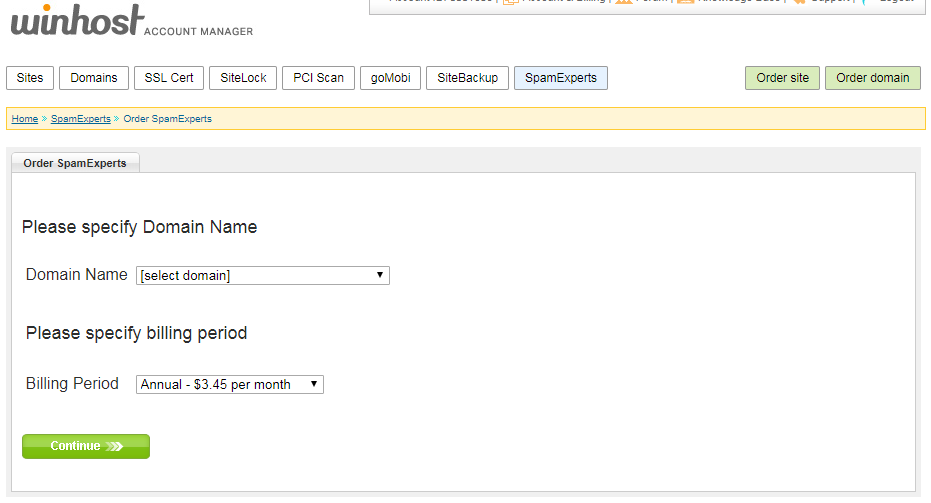
On the next page, you can set where SpamExperts will send your email after filtering. Our system will look up the current email servers for your domain. This will be the correct setting for most users.
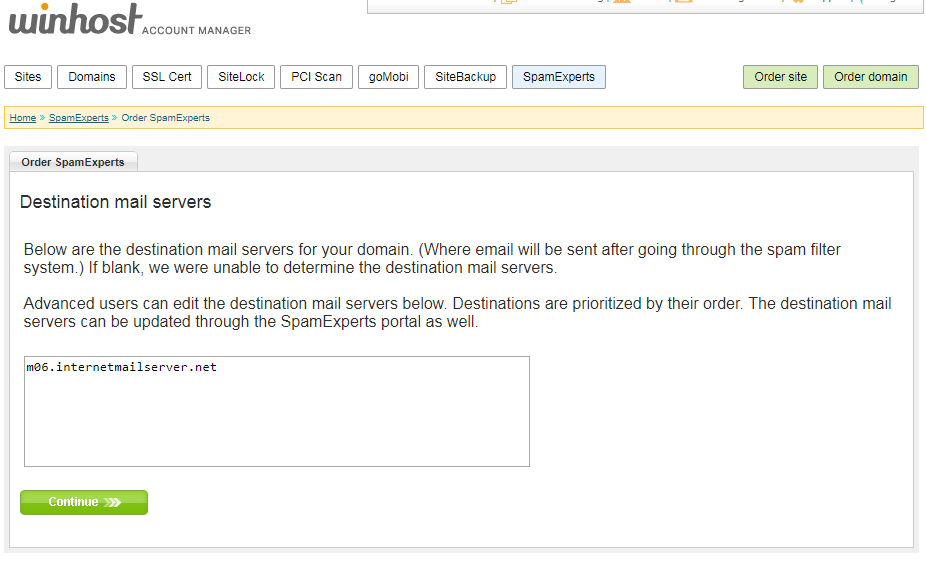
The service will only take a few seconds to set up. Now you have to set up your domain mail records (MX Records) to point to the SpamExperts service.
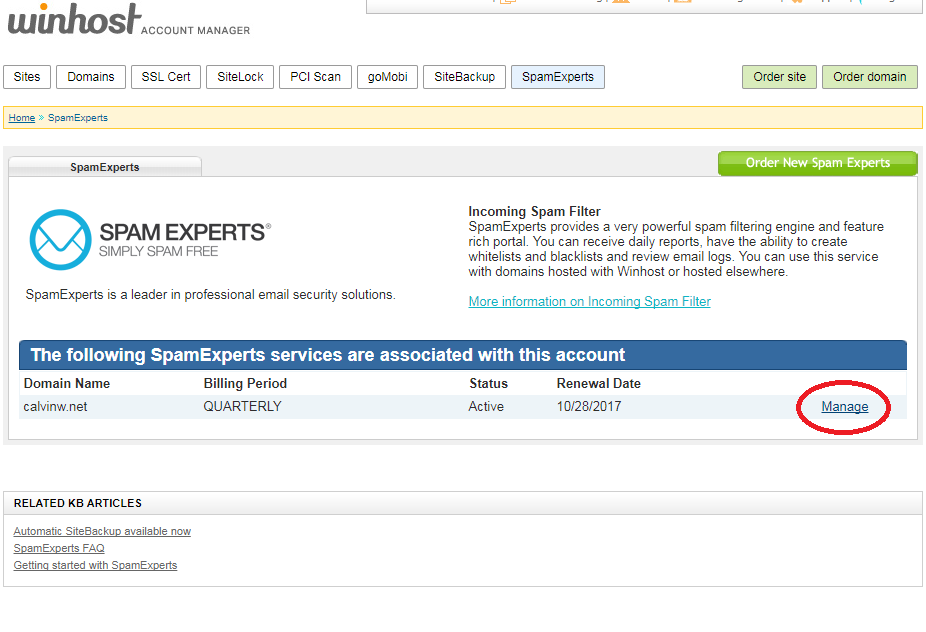
On the next page, you’ll see the SpamExperts MX Records to use. If you are using our nameservers, our system will automatically set up the MX Records for you.
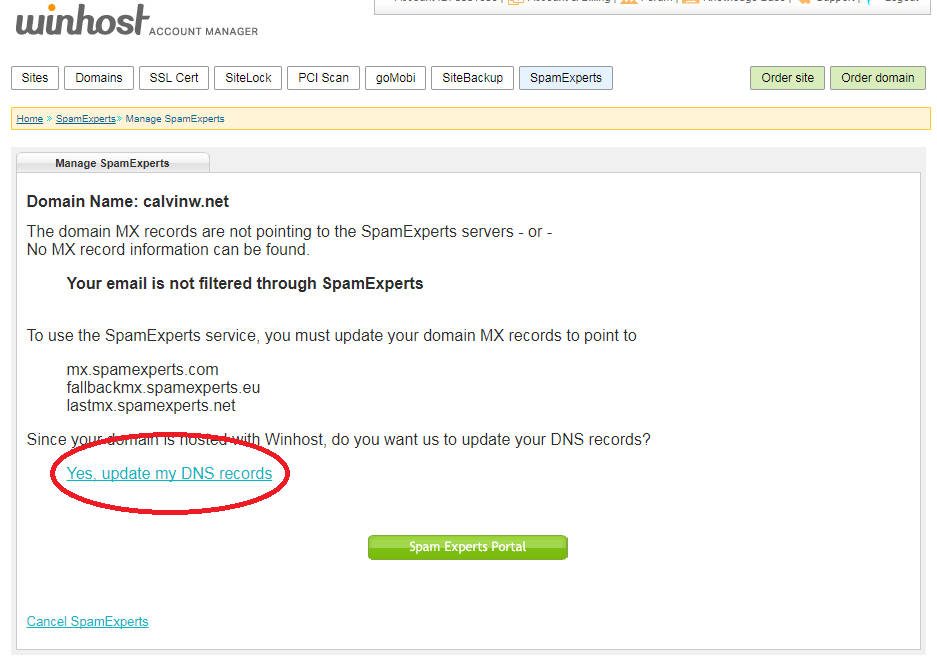
And you’re all set! Again, SpamExperts works great out of the box. If you’re so inclined, you can click the green SpamExpert Portal button to get the SpamExperts interface to make changes to the service settings.
A note about Greylisting: Greylisting is an effective anti-spam function that we enable in SmarterMail by default. Greylisting can delay when you receive new emails. Disabling Greylisting gets rid of the delay, but likely results in much getting more spam. With SpamExperts filtering out spam, you can disable Greylisting in SmarterMail. No spam, no delay. Yay!
![]()
SiteBackup is a set-it-and-forget-it backup service that will automatically backup your website and database. Backups are stored in a remote location and previous versions can be restored to the web server with just a click. Here are instructions on how to order and set up SiteBackup.
You can order SiteBackup through your Winhost Control Panel. We offer three plans, each with different storage amounts. You only need one SiteBackup plan to back up all of your sites, so just pick the plan with enough storage to cover your sites. Click the orange button to select the plan you want, then click the Submit My Order button on the next page.
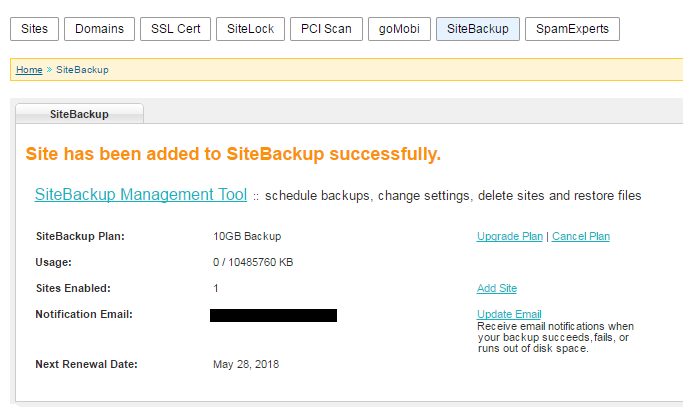
It takes a few minutes for our system to provision the service. You can click the Back button or the SiteBackup tab, and if the service is ready, you’ll see this page, where you can add a site:
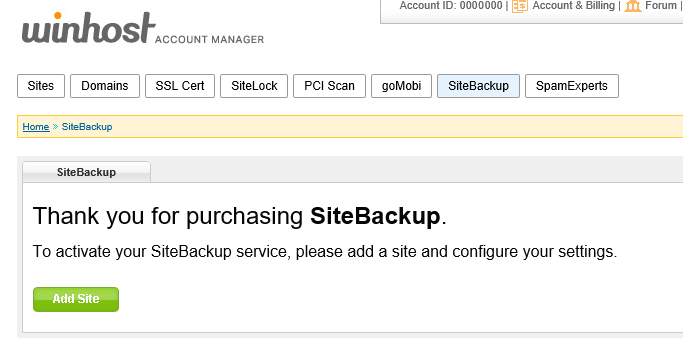
Click the Add Site button and on the next page you can select the sites you want to back up.
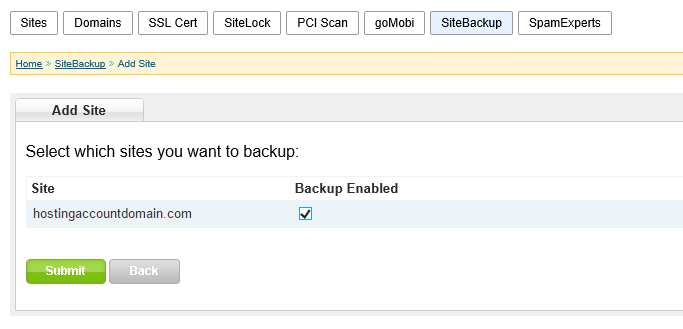
Select which site(s) you want to back up, click the Submit button, and our system will automatically pass along the required info. On the next page, you can click the SiteBackup Management Tool link to get to the SiteBackup Dashboard interface.
On the SiteBackup Dashboard, you can configure your backup schedule. By default, there will be a daily backup scheduled. You can keep that, change the backup time, change the backup frequency, and run an immediate backup.
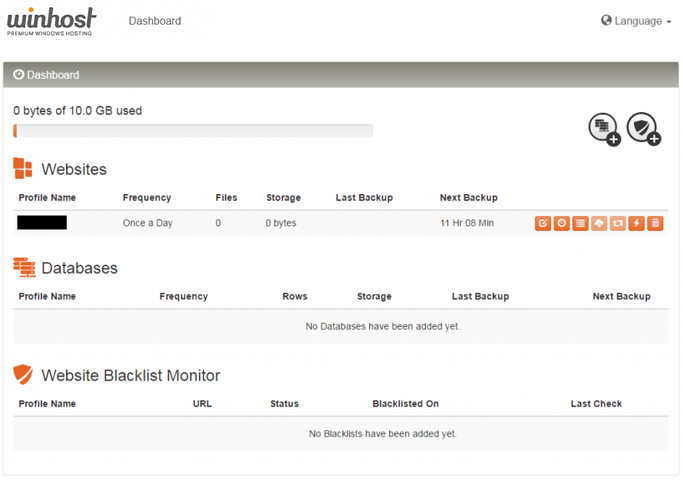
You can also back up your databases (the example in that Knowledge Base article is an MS SQL database, but SiteBackup can also back up your MySQL databases).
The system will email you if a backup fails (like when you change the FTP password). So just keep an eye out for those emails. But other than that, it’s set and you can forget it.